Most british forensic investigations risk evidence being thrown out when simple preparation steps are overlooked. For specialists in London, maintaining the chain of custody and using write blockers can make the difference between a solid case and wasted effort. This guide walks through every technique and protocol, delivering clear tools to ensure digital evidence stands up to scrutiny for both legal and corporate clients.
Table of Contents
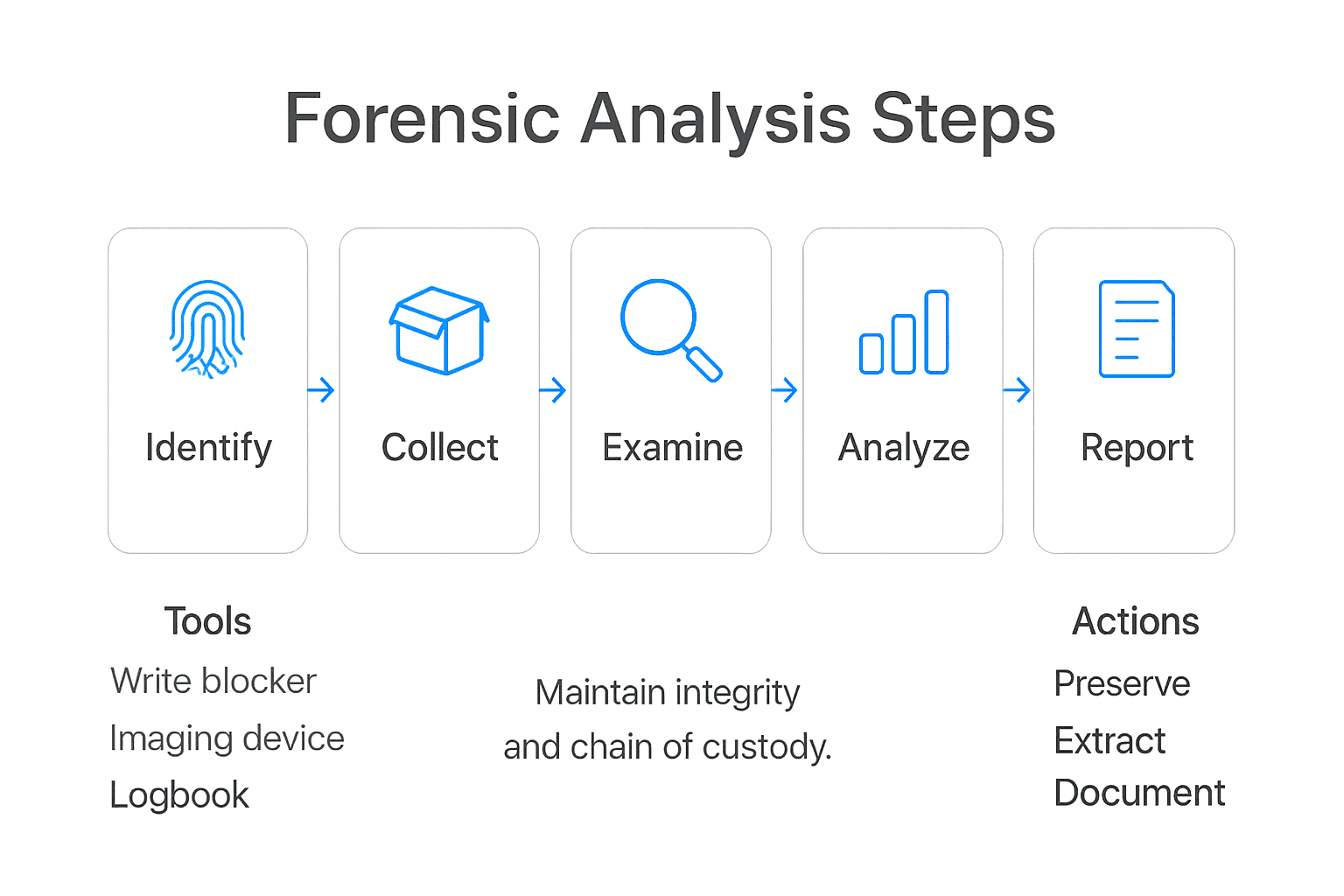
- Step 1: Prepare Forensic Tools And Secure Evidence
- Step 2: Preserve Digital Evidence With Integrity
- Step 3: Extract And Analyse Relevant Data
- Step 4: Document Findings And Maintain Chain Of Custody
- Step 5: Present Results In Expert Witness Reports
Quick Summary
| Key Insight | Explanation |
|---|---|
| 1. Prepare forensic tools meticulously | Collect precise tools and document protocols to ensure evidence integrity during collection. |
| 2. Preserve evidence with strict protocols | Implement rigorous methods to maintain original data integrity and avoid contamination throughout the investigation. |
| 3. Systematically extract and analyse data | Use scientific techniques to interpret digital evidence, ensuring validity and maintaining evidence integrity during extraction. |
| 4. Document findings and chain of custody | Maintain comprehensive logs and proper documentation of evidence handling to ensure legal admissibility. |
| 5. Present results clearly in reports | Create expert witness reports that articulate findings and methodologies in a clear manner for legal professionals. |
Step 1: Prepare forensic tools and secure evidence
Forensic analysis begins with meticulous preparation of specialised tools and establishing strict evidence preservation protocols. This crucial initial stage ensures the integrity and admissibility of digital evidence in legal proceedings.
To start, gather your forensic toolkit which must include write blockers, forensic imaging devices, write-protected external storage, forensically sanitised computers, evidence collection bags, documentation forms, and chain of custody tracking sheets. These tools prevent accidental data modification during evidence acquisition. Initial digital evidence collection protocols recommend creating a comprehensive inventory of all equipment and establishing clear handling procedures before commencing any investigation.
Prioritise creating a controlled, secure environment for evidence collection. This means isolating digital devices from network connections, using electrostatic protective bags for electronic media, and documenting every action with precise timestamped notes. Wear clean gloves, use anti static mats, and ensure your workspace is free from potential contamination sources that could compromise forensic evidence.
To clarify the benefits of key forensic tools, see this summary table:
| Forensic Tool | Primary Purpose | Impact on Investigation |
|---|---|---|
| Write blocker | Prevents data alteration | Ensures evidence authenticity |
| Forensic imaging device | Creates exact digital copy | Enables repeatable analysis |
| Documented chain of custody | Tracks evidence handling | Maintains legal admissibility |
| Electrostatic protective bag | Shields electronic media from damage | Preserves physical integrity |
Expert Recommendation: Always create forensic images immediately upon device seizure to prevent potential data loss or accidental alteration during extended investigations.
Step 2: Preserve digital evidence with integrity
Preserving digital evidence requires a systematic approach that maintains the original data’s integrity while protecting it from potential contamination or unintentional modification. This critical stage ensures that digital artifacts remain legally admissible and scientifically valid throughout the investigative process.
Begin by implementing rigorous protocols for handling digital evidence that prioritise data protection. This involves creating forensic duplicates of original media using write blockers to prevent any inadvertent modifications, documenting each device’s condition through detailed photographs and comprehensive notes, and establishing an immediate chain of custody tracking. Your preservation strategy must account for volatile data first, capturing system memory, active network connections, and running processes before they potentially disappear or change.
Maintain a meticulous preservation environment by controlling physical access to evidence, using anti static bags for electronic devices, and storing digital media in controlled temperature conditions away from magnetic interference. Record every single action with timestamped documentation, including device serial numbers, acquisition methods, and precise location information. Ensure all team members wear protective gloves, use forensically sanitised equipment, and follow strict contamination prevention protocols.
Expert Recommendation: Always create multiple forensic image copies stored on write protected media in separate secure locations to guarantee data redundancy and protection against potential media failure.
Step 3: Extract and analyse relevant data
Data extraction represents the most critical phase of digital forensic investigation where systematic scientific methods transform raw digital artifacts into meaningful investigative insights. Your objective is to methodically uncover and interpret digital evidence that can substantiate or refute specific investigative hypotheses.
Digital forensic analysis requires a disciplined approach to systematically searching collected digital evidence. Begin by categorising data sources hierarchically prioritising volatile data sources such as system memory, active network connections, and running processes. Utilise specialised forensic software tools capable of creating forensically sound bit stream images, recovering deleted files, extracting metadata, and performing comprehensive file system analysis. Pay meticulous attention to maintaining evidence integrity throughout the extraction process, documenting every action with precise timestamped notes and capturing forensic hash values to verify data authenticity.
Carefully examine recovered data across multiple dimensions examining file timestamps, user activity logs, internet browsing history, communication records, and application metadata. Cross reference findings to build a comprehensive narrative of digital events, looking for patterns, anomalies, and potential connections that might reveal critical investigative insights. Validate your analysis through reproducible scientific methodologies, ensuring that your extraction and interpretation processes can withstand rigorous legal and technical scrutiny.
Expert Recommendation: Always maintain a comprehensive forensic log documenting every technical action performed during data extraction to ensure transparency and potential courtroom admissibility.
Step 4: Document findings and maintain chain of custody
Documenting forensic findings and maintaining an unbroken chain of custody represents the most critical legal safeguard in digital evidence preservation. Your meticulous documentation will determine whether evidence can be admitted in legal proceedings and withstand potential challenges.
Establish a comprehensive chain of custody tracking system that chronicles every single interaction with digital evidence. Create detailed logs recording the precise time, date, personnel involved, and purpose of each evidence transfer or examination. Use forensically validated tracking forms that capture unique identifiers for each piece of digital media, including device serial numbers, forensic hash values, and acquisition timestamps. Implement a robust access control system that restricts evidence handling to authorised personnel only, maintaining a sequential record of every individual who accessed or modified the evidence.
Prepare meticulous forensic reports that transparently communicate your methodological approach, analysis techniques, and substantive findings. Include comprehensive technical documentation explaining your forensic tools, examination procedures, and validation methods. Ensure that your documentation is sufficiently detailed for independent experts to reproduce your analysis and verify your conclusions. Organise findings logically, presenting digital evidence with clear contextual explanations that demonstrate how recovered data supports or refutes specific investigative hypotheses.
Expert Recommendation: Always create redundant documentation backups stored in separate secure locations to protect against potential record loss or corruption.
Step 5: Present results in expert witness reports
Preparing expert witness reports represents the crucial final stage of digital forensic analysis where scientific findings are transformed into legally comprehensible documentation. Your objective is to communicate complex technical findings in a clear, credible manner that can withstand rigorous legal scrutiny.
Federal legal guidelines for expert witness reporting require comprehensive documentation that transparently articulates your forensic methodologies, findings, and professional conclusions. Craft your report with meticulous precision, including a detailed statement of your expert opinions, the scientific basis for those opinions, specific facts considered during analysis, and a comprehensive list of reference materials and exhibits. Clearly outline your professional qualifications, highlighting relevant academic credentials, professional certifications, and prior forensic experience to establish your credibility and expertise.
Structure your report to guide legal professionals through your investigative process, presenting technical findings in a logical sequence that demonstrates how digital evidence supports specific legal hypotheses. Use clear, unambiguous language that avoids unnecessary technical jargon, ensuring that judges, lawyers, and juries can understand your conclusions. Include visual aids such as annotated screenshots, timeline graphics, and data flow diagrams to enhance comprehension. Anticipate potential challenges by thoroughly documenting your methodology, ensuring that every claim is substantiated by reproducible forensic techniques and verifiable digital evidence.
For a structured overview, compare forensic report elements with courtroom requirements below:
| Report Element | Forensic Purpose | Legal Importance |
|---|---|---|
| Evidence summary | Details digital findings | Guides judge and jury |
| Method documentation | Explains acquisition, analysis steps | Verifies scientific validity |
| Expert qualifications | Establishes analyst’s credibility | Supports expert witness status |
| Reference exhibits | Provides supporting materials | Enables independent verification |
Expert Recommendation: Always have a senior forensic expert review your report for clarity, technical accuracy, and potential legal vulnerabilities before submission.
Enhance Your Legal Cases With Expert Digital Forensics Support
Conducting a thorough forensic analysis for legal evidence requires precise handling of digital data, rigorous documentation, and maintaining an unbroken chain of custody. If you face challenges in preserving evidence integrity, extracting meaningful data, or preparing expert witness reports that withstand courtroom scrutiny, you are not alone. These critical steps demand advanced forensic tools and specialist knowledge to ensure evidence is legally admissible and technically sound.
At Computer Forensics Lab, we understand the vital importance of each phase in your forensic investigation. Our expert team provides comprehensive Digital Forensics services designed to safeguard your evidence with professional chain of custody protocols detailed in our Chain of Custody Tracking solutions. Whether it is recovering deleted files, analysing complex digital trails, or delivering clear, authoritative expert witness reports, we support your legal and investigative needs with unmatched expertise.
Secure your case by partnering with specialists who prioritise precision and legal compliance. Visit Computer Forensics Lab now to learn how our computer forensics and digital evidence services can protect your evidence’s integrity and strengthen your legal strategy.
Frequently Asked Questions
What are the essential forensic tools needed for legal evidence analysis?
To conduct a thorough forensic analysis, essential tools include write blockers, forensic imaging devices, and write-protected external storage. Start by assembling these tools to ensure data integrity and prevent accidental modification during evidence acquisition.
How do I preserve digital evidence to maintain its integrity?
Preserve digital evidence by creating forensic duplicates using write blockers and meticulously documenting each device’s condition. Implement strict handling protocols and timestamp all actions to maintain a clear chain of custody.
What steps should I take to extract and analyse data from digital evidence?
Begin data extraction by categorising data sources, prioritising volatile data first, and using specialised forensic software tools. Carefully document each action taken during extraction to ensure transparency and maintain evidence integrity throughout the process.
How can I maintain an effective chain of custody for digital evidence?
Maintain an effective chain of custody by creating detailed logs that record every interaction with digital evidence, including times, personnel involved, and purposes of transfers. Implement a robust access control procedure to restrict evidence handling to authorised individuals only.
What should I include in an expert witness report for forensic analysis?
Include key elements such as a summary of evidence, documentation of methods used, and your professional qualifications in an expert witness report. Clearly structure the report to present findings logically, supporting your conclusions with reproducible forensic techniques.
How can I ensure my forensic report withstands legal scrutiny?
Ensure your forensic report is comprehensive by having it reviewed by a senior expert for clarity and technical accuracy. Document every aspect of your methodology and include visual aids to help convey complex information effectively.