Over 95 percent of legal cases today involve some form of digital evidence, making forensic data recovery a crucial tool for british investigators and legal teams. With electronic devices woven into nearly every aspect of modern life, understanding how professionals recover and protect digital information matters more than ever. This guide reveals the core processes, legal considerations, and vital best practices that set british forensic experts apart when preserving digital evidence for court.
Table of Contents
- Defining Forensic Data Recovery And Core Concepts
- Types Of Devices And Data Recovered
- How The Forensic Data Recovery Process Works
- Legal Principles And Chain Of Custody Requirements
- Risks, Challenges, And Best Practice Protocols
Key Takeaways
| Point | Details |
|---|---|
| Forensic Data Recovery Defined | A systematic process for retrieving, preserving, and analysing electronic data for legal purposes, ensuring the integrity and admissibility of digital evidence. |
| Range of Devices and Evidence | Investigations cover various devices including smartphones and computers, each presenting unique challenges for evidence recovery. |
| Stages of the Recovery Process | The recovery process follows strict protocols: identification, preservation, acquisition, analysis, and reporting, to maintain data integrity. |
| Legal and Best Practice Protocols | Adhering to documented procedures, maintaining the chain of custody, and continuous training are essential to address challenges and ensure evidence integrity. |
Defining Forensic Data Recovery and Core Concepts
Forensic data recovery is a systematic digital investigation process designed to retrieve, preserve, and analyse electronic data for legal and investigative purposes. According to ijert.org, digital forensics involves identifying, collecting, analyzing, and reporting digital information from electronic devices with meticulous precision.
At its core, forensic data recovery goes beyond simple file retrieval. The process requires specialist techniques to extract digital evidence while maintaining strict chain of custody protocols. Investigators must ensure that recovered data remains legally admissible, which means protecting the original digital artifacts from contamination or modification. As ijcttjournal.org highlights, this is particularly critical in mobile forensics, where data extraction demands constant technological adaptation and legal compliance.
The fundamental objectives of forensic data recovery encompass several critical dimensions:
- Evidence Preservation: Maintaining the integrity of digital artifacts without altering original data
- Comprehensive Analysis: Extracting hidden or deleted information from various electronic devices
- Legal Compliance: Ensuring all recovered data meets forensic and legal standards for potential court proceedings
- Investigative Support: Providing actionable insights for criminal, civil, and corporate investigations
Forensic data recovery professionals utilise advanced technological tools and methodological approaches to navigate complex digital landscapes, transforming raw electronic data into meaningful legal evidence. Their work bridges technological expertise with legal requirements, making them crucial players in modern investigative processes.
Types of Devices and Data Recovered
Digital forensic investigations encompass a wide range of electronic devices and data sources, each presenting unique challenges and opportunities for evidence recovery. According to ijert.org, digital forensics involves multiple device types including computers, mobile phones, and network systems, each requiring specialised recovery techniques.
ijcttjournal.org highlights the complexity of mobile forensic tools, emphasising that modern data recovery goes far beyond simple file extraction. The range of recoverable digital evidence is remarkably diverse:
- Smartphones: Messages, call logs, GPS locations, application data
- Computers: Email archives, browsing history, deleted documents, system logs
- Cloud Storage: Remote data repositories, synchronised files, backup archives
- Network Devices: Router logs, connection records, transmission metadata
- Social Media Platforms: Direct messages, interaction histories, multimedia content
The forensic data recovery process demands forensic specialists be adept at navigating multiple digital ecosystems. Whether investigating corporate misconduct, criminal activities, or civil litigation, professionals must employ sophisticated mobile phone physical data extraction and recovery techniques to uncover critical digital evidence that might otherwise remain hidden.
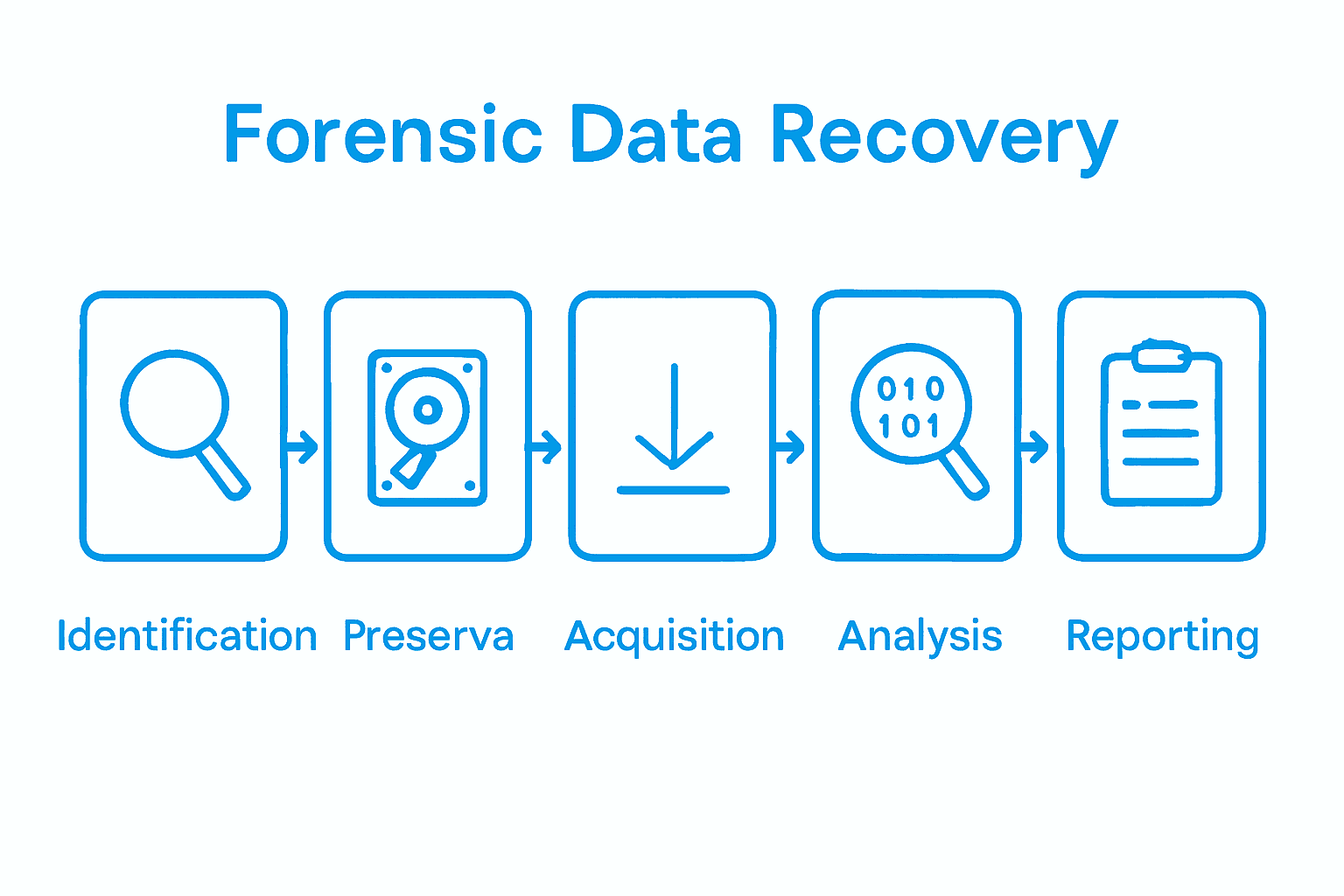
How the Forensic Data Recovery Process Works
Forensic data recovery is a meticulous, multi-stage process that transforms digital artifacts into legally admissible evidence. According to ijcttjournal.org, the mobile forensic investigation process follows a structured approach designed to maintain data integrity and ensure comprehensive evidence collection.
ijert.org outlines the fundamental stages of digital forensic investigations, which can be broken down into precise sequential steps:
- Identification: Locating potential digital sources of evidence
- Preservation: Creating forensically sound bit-by-bit copies of digital media
- Acquisition: Extracting data while maintaining original evidence integrity
- Analysis: Examining recovered data for relevant investigative insights
- Reporting: Documenting findings in a legally defensible manner
Professionals must adhere to strict chain of custody protocols, ensuring every step is documented and verifiable. For legal teams seeking deeper insights, our guide on essential forensic data recovery steps provides a comprehensive overview of navigating these complex investigative techniques. Each stage requires specialized tools, technical expertise, and an unwavering commitment to preserving the authenticity of digital evidence.
Legal Principles and Chain of Custody Requirements
Forensic data recovery operates within a stringent legal framework that demands absolute precision and integrity. According to ijcttjournal.org, maintaining a proper chain of custody is critical to ensuring the admissibility of digital evidence in legal proceedings, particularly in mobile forensics investigations.
ijert.org emphasizes the fundamental legal principles that govern digital forensic work, highlighting several key requirements:
- Documented Procedures: Every action must be meticulously recorded
- Evidence Preservation: Original digital artifacts must remain unaltered
- Authentication: Verifiable proof of evidence origin and handling
- Integrity Verification: Consistent methods to confirm data authenticity
- Comprehensive Reporting: Detailed documentation of forensic processes
The legal landscape demands forensic professionals maintain an unbroken chain of custody, which means tracking every single interaction with digital evidence. For legal teams seeking a comprehensive understanding, our guide to digital forensics chain of custody provides critical insights into navigating these complex legal requirements. Failure to adhere to these principles can render even the most critical digital evidence inadmissible in court, underscoring the paramount importance of forensic precision.
Risks, Challenges, and Best Practice Protocols
Digital forensic investigations confront an ever-evolving landscape of technological challenges and potential risks. According to ijcttjournal.org, mobile forensics faces significant obstacles including device encryption, rapid technological advancements, and the inherent volatility of digital data.
ijert.org highlights critical risks that forensic professionals must navigate carefully:
- Technological Complexity: Constantly changing device architectures
- Data Encryption: Advanced security measures blocking evidence access
- Rapid Obsolescence: Tools becoming quickly outdated
- Data Manipulation Risks: Potential for unintentional evidence corruption
- Cybersecurity Threats: Emerging techniques designed to prevent forensic examination
Best practice protocols demand a proactive and comprehensive approach to mitigating these challenges. Forensic teams must invest in continuous training, maintain multiple forensic tools, and develop adaptive strategies. Professionals seeking deeper insights can explore our comprehensive digital forensics techniques tutorial, which offers advanced strategies for navigating these complex investigative landscapes. The key is maintaining flexibility, technical expertise, and an unwavering commitment to forensic integrity.
Expert Forensic Data Recovery Support When You Need It Most
Forensic data recovery is a critical and delicate process that requires precision to preserve digital evidence and maintain an unbroken chain of custody. Whether you face challenges with encrypted devices, hidden or deleted data, or complex mobile phone extractions, understanding the significance of these technical and legal hurdles can be overwhelming. At Computer Forensics Lab, we specialise in helping legal professionals, businesses, and private clients navigate these complexities with confidence.
Our team of Forensic Data Specialists and Forensic Mobile Experts use advanced techniques tailored to ensure integrity and admissibility of your digital evidence. Don’t let vital information remain inaccessible or compromised. Visit Computer Forensics Lab today to discover how our expert forensic data recovery services can empower your investigations and support your legal needs with accuracy and professionalism.
Frequently Asked Questions
What is forensic data recovery?
Forensic data recovery is a systematic digital investigation process that aims to retrieve, preserve, and analyse electronic data for legal and investigative purposes.
Why is chain of custody important in forensic data recovery?
Chain of custody is crucial as it ensures that recovered digital evidence remains legally admissible in court by protecting original artifacts from contamination or modification.
What types of data can be recovered during a forensic investigation?
Data that can be recovered includes messages, call logs, browsing history, deleted documents, GPS locations, cloud storage files, router logs, and more from various electronic devices including smartphones and computers.
What are the main steps involved in the forensic data recovery process?
The key stages are identification, preservation, acquisition, analysis, and reporting, each requiring meticulous attention to maintain data integrity and ensure comprehensive evidence collection.