::contentReference[oaicite:0]{index=0}
Recovery and extraction of data from disabled, dead, damaged, PIN-protected, encrypted and/or password protected mobile phones and tablets
Do you have a disabled, PIN-locked, dead/damaged or encrypted mobile device and you want a fully accessible, unencrypted forensic physical data extraction to be used in your digital forensic investigation? Computer Forensics Lab can help you.
Computer Forensics Lab digital forensic experts are among the very select few who have access to the Greykey, MSAB XRY, Cellebrite InSeyts Enterprise UFED and Cellebrite Physical Analyzer. In addition to this, our lab is equipped with Ace Labs PC3000 HDD, SSD and NAND Flash advanced data recovery hardware and software suite. We also have our own advanced in-house hardware and software forensic tools for JTAG and chip-off physical recovery of data from mobile handsets, memory cards, memory sticks and NAND flash and ROM chips. This enables our experts to assist law enforcement, government agencies, UK Crown Prosecution Service, and Crown Courts to uncover evidence from modern highly secure and encrypted mobile devices, even if the password and/or the PIN of these devices is not known or were not given by the defendant or the device is disabled or dead.
If you are in possession of a dead, damaged, disabled, PIN-locked, encrypted and/or password protected mobile phone, tablet or laptop running Android, iOS or the latest MacOS, Computer Forensics Lab’s digital forensic team, can unlock and decrypt these devices and extract all the data in full by making it available for further digital forensic examination and analysis.
Our expertise extends to all old and new generation of mobile phones and as well as the most recent models of iPhones, iPads, Motorola, Google Pixel, LG, Samsung handsets and tabs including Chinese brands such as One Plus, Huawei, Oppo, Xiaomi, Lenovo, RealMe, ZTE, Poco, Tecno and Honor.
As long as proper authorisation from law enforcement and/or the courts is presented to us, our digital forensic analysts will be able to do a full physical extraction of data from the encrypted volumes in different mobile devices.
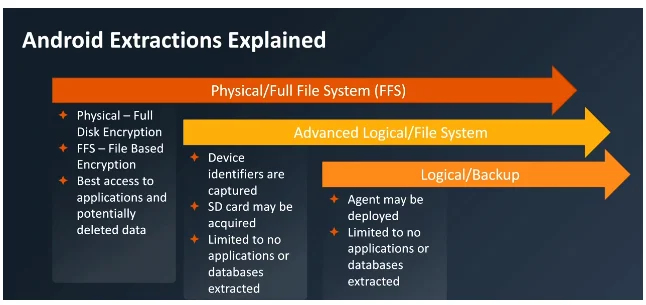
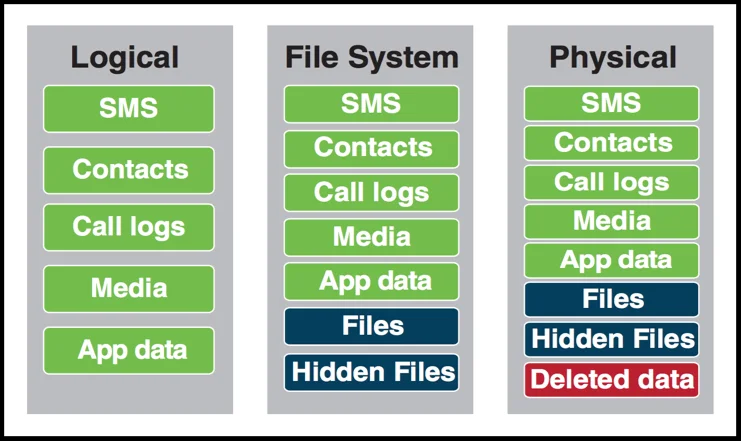
- The full forensic physical extraction of mobile devices will contain all Operating System data plus the user data with all the logs and app events along with geolocation information, date and timestamps of all user activities without any omission.
- Furthermore, Computer Forensics Lab experts can carve and recover deleted data from all types of mobile handsets. The advanced in-house hardware and software data extraction and recovery tools at our disposal, enable us to ensure that no critical digital evidence is hidden from the keen eyes of the digital forensic examiner. It is important to note that missing or incomplete extraction of data from seized or acquired mobile handsets and computers, can adversely affect the results of a digital forensic investigation and can lead to miscarriage of justice. Full disclosure of all data from mobile handsets is only possible if a physical data acquisition of the mobile device or a computer is performed whether or not the pin or password of the mobile device or the computer is known or not given.
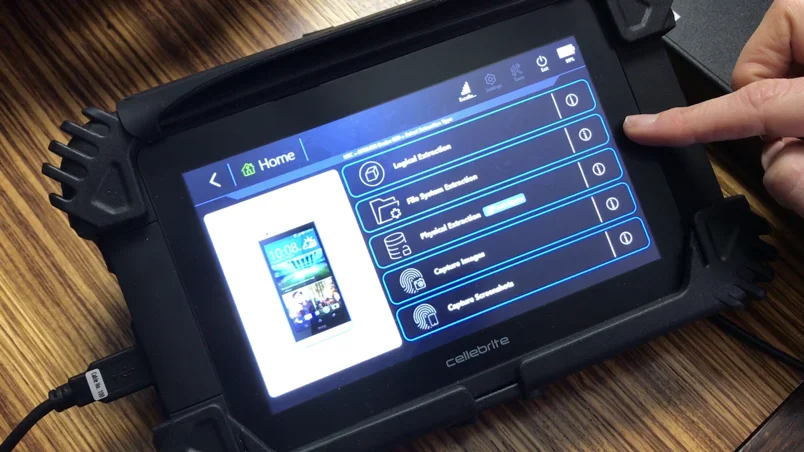
How does physical data extraction work in mobile devices?
Fundamentally, physical data extraction in mobile devices bypasses the device’s Operating System (OS). This is carried out just before the OS of device starts to set in. The stage is called the Bootloader which is the first thing that starts up when a device is turned on. In this method, bootloaders, can bypass system locks and passcodes to extract deleted passwords, files, photos, videos, text messages, call logs, GPS tags, and other artifacts. After a physical extraction there are no signs of an investigation once it is complete. The data is left forensically intact to ensure the investigation is not compromised.
IMPORTANT NOTE:
For forensic data recovery and physical data extraction of mobile devices whose PINs and/or passwords are not known or have not been provided, prior authorisation from a legal authority (such as a warrant or court order) is required, This service is only available to authorised legal professionals, law enforcement, Crown Prosecution Service and/or public enquiries. Private individuals or companies who want to use this restricted service must provide a warrant or a court order and/or verified proof of ownership of the mobile device. Without this, Computer Forensics Lab will not be able to perform a physical data extraction from an encrypted, PIN or password-protected mobile device.
Prosecution, public bodies, law enforcement ,attorneys, solicitors, barristers, digital forensic firms and mobile forensic examiners can contact us for assistance in physical acquisition of data from any type of PIN-locked, encrypted mobile phones by calling 02071646915. In cases where the PIN is not given or not known, prior legal authority in the form of a warrant or court order is required.