Over 97 percent of adults now own a mobile device, making smartphones a prime source of crucial evidence in both criminal and civil cases. As technology grows more secure, extracting digital evidence from modern devices has become a complex challenge for forensic professionals. Discover how cutting-edge techniques and strict legal requirements shape the way experts recover and protect sensitive digital data during investigations.
Table of Contents
- Defining Digital Forensic Data Extraction
- Modern Mobile Operating Systems And Encryption
- Technical Barriers In Iphone And Android Forensics
- Legal And Regulatory Constraints On Data Access
- Emerging Solutions And Industry Best Practices
Key Takeaways
| Point | Details |
|---|---|
| Digital Forensic Data Extraction | It involves carefully recovering digital evidence while preserving integrity and ensuring legal admissibility through structured protocols. |
| Modern Mobile Security Challenges | Current mobile operating systems employ advanced encryption, creating complex barriers for forensic data extraction that require specialized knowledge. |
| Legal Constraints on Forensics | Digital forensic investigations must navigate intricate legal frameworks that balance user privacy rights with law enforcement needs, impacting data access methods. |
| Emerging Solutions & Best Practices | Industry best practices are shifting towards proactive security measures and the development of advanced decryption techniques to enhance forensic readiness. |
Defining Digital Forensic Data Extraction
Digital forensic data extraction represents a sophisticated investigative process for retrieving and analysing digital evidence from electronic devices. According to Commons Digital Forensics Research, this systematic methodology involves methodically recovering data to support legal investigations while maintaining strict forensic standards.
The core objective of digital forensic data extraction is to uncover critical information without compromising its original state or integrity. ArXiv Research emphasises that this process encompasses structured retrieval techniques designed to ensure data preservation and legal admissibility. Forensic experts must follow precise protocols to extract digital artifacts that can potentially serve as crucial evidence in criminal or civil proceedings.
Key components of digital forensic data extraction include:
- Preservation of original data integrity
- Forensically sound acquisition techniques
- Comprehensive documentation of extraction processes
- Chain of custody maintenance
- Advanced technological tools and methodological approaches
Understanding the intricacies of mobile phone physical data extraction requires specialised knowledge and cutting-edge technological capabilities. Forensic professionals must navigate complex digital landscapes, employing sophisticated techniques to retrieve valuable digital evidence while adhering to stringent legal and ethical standards.
Modern Mobile Operating Systems and Encryption
Modern mobile operating systems have revolutionised digital security through advanced file-based encryption mechanisms. According to ArXiv Research, these systems implement sophisticated key derivation processes designed to protect user data comprehensively, creating multiple layers of security that challenge traditional data extraction methods.
SES Journal Research highlights that contemporary mobile operating systems like Android and iOS have integrated encryption approaches specifically engineered to address evolving cyber threats. These systems do not merely encrypt entire device storage but employ granular encryption strategies that protect individual files and user-specific data compartments, making forensic data retrieval increasingly complex.
Key encryption strategies in modern mobile operating systems include:
- Unique device-specific encryption keys
- Biometric and passcode-linked decryption mechanisms
- Hardware-backed keystore protections
- Secure enclave technologies
- Kernel-level security implementations
Forensic professionals seeking to extract data must now navigate intricate cryptographic landscapes. Understanding Android forensics methods becomes crucial, as each operating system presents distinct encryption challenges that require specialised technological approaches and deep technical expertise to overcome.
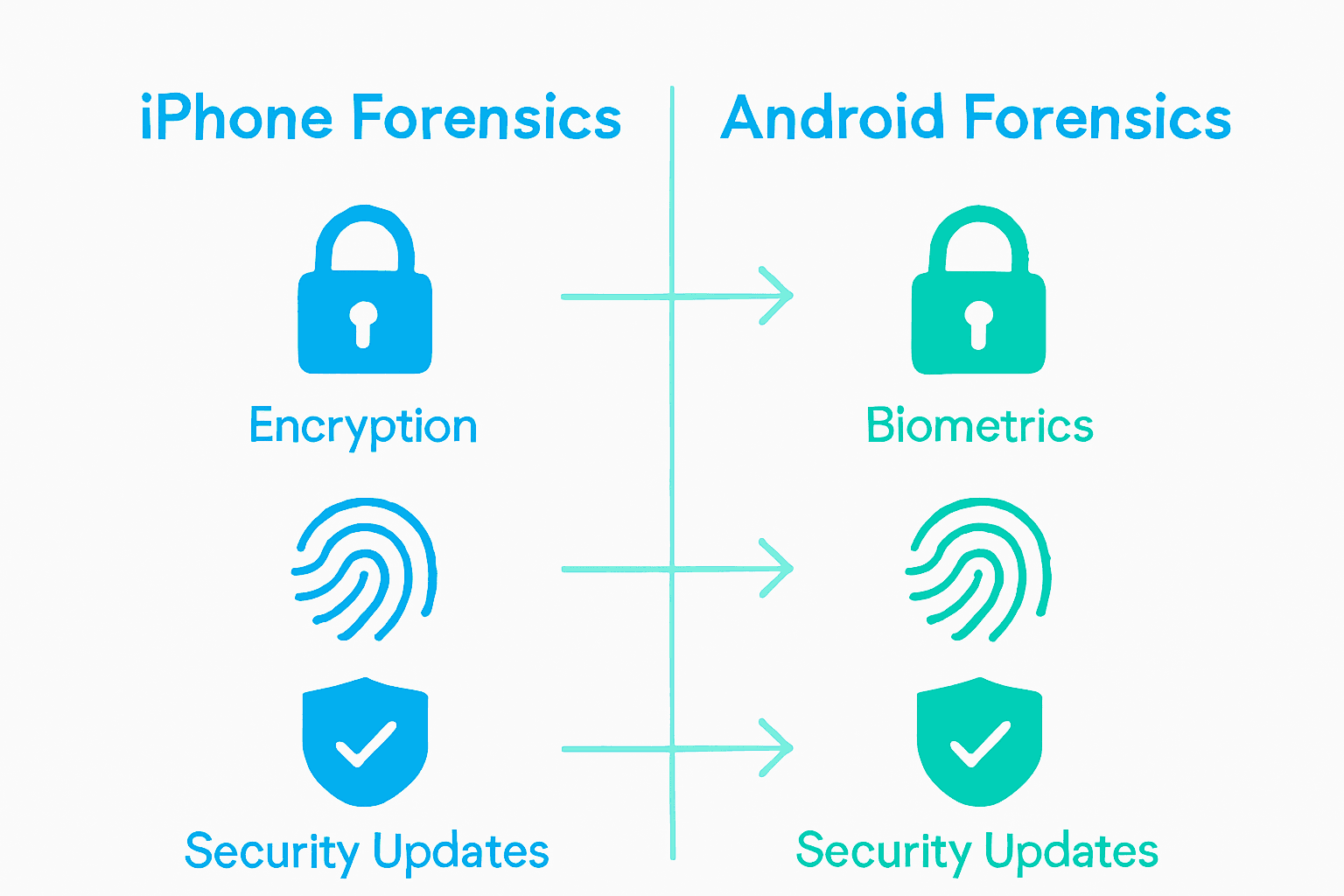
Technical Barriers in iPhone and Android Forensics
Mobile device forensics has become increasingly challenging due to sophisticated security architectures in modern smartphones. ArXiv Research highlights that forensic analysis of iPhone and Android devices now confronts unprecedented technical barriers, with advanced encryption and security measures systematically hindering traditional data extraction methodologies.
The implementation of full disk encryption has fundamentally transformed digital forensic investigations. According to ArXiv Research, plausibly deniable encryption systems have introduced significant technical complexities that compromise conventional data retrieval processes. These sophisticated security mechanisms create multi-layered protection schemes that require forensic experts to develop increasingly advanced technological approaches.
Key technical barriers in mobile device forensics include:
Here is a comparison of the primary technical barriers encountered in iPhone and Android forensics:
| Technical Barrier | iPhone Forensics | Android Forensics |
|---|---|---|
| Hardware Encryption | Secure Enclave technology | Device-specific key storage |
| Biometric Authentication | Face ID Touch ID |
Fingerprint Face unlock |
| Encryption Type | File-based with hardware tie-in | File-based Disk-level |
| Key Management | Advanced key hierarchy | Dynamic key generation |
| Security Updates | Frequent, unified roll-out | Staggered, OEM dependent |
| Secure Boot & Trusted Execution | Mandatory & robust | Varies across manufacturers |
- Sophisticated hardware-level encryption
- Biometric authentication complexities
- Secure enclave technologies
- Advanced key management systems
- Dynamic encryption key generation
Navigating these intricate forensic challenges requires deep technological expertise.

Legal and Regulatory Constraints on Data Access
Digital forensic investigations now operate within increasingly complex legal frameworks that dramatically impact data extraction methodologies. ArXiv Research emphasises that contemporary legal regulations meticulously balance user privacy rights against the investigative requirements of law enforcement agencies, creating nuanced constraints on digital evidence acquisition.
Regulatory policies have fundamentally transformed the landscape of digital forensics. According to ArXiv Research, forensic experts must navigate intricate legal considerations that significantly influence the methods and extent of data analysis from encrypted mobile devices. These regulatory constraints demand sophisticated approaches that respect individual privacy while maintaining the integrity of potential digital evidence.
Key legal and regulatory considerations include:
- Warrant requirements for device access
- Protection of individual privacy rights
- Jurisdictional variations in digital evidence laws
- Consent protocols for data extraction
- Chain of evidence preservation standards
- Protection against unreasonable search and seizure
Understanding these complex legal boundaries requires specialised knowledge. Challenges in digital forensics investigations become crucial for professionals seeking to navigate the intricate intersection of technological capabilities and legal constraints, ensuring forensic practices remain both legally defensible and ethically sound.
Emerging Solutions and Industry Best Practices
Digital forensic technology continues to evolve rapidly in response to increasingly sophisticated mobile device security challenges. ArXiv Research highlights the development of advanced decryption techniques and standardized frameworks that are expanding data extraction capabilities for forensic professionals across various investigative contexts.
Industry best practices are increasingly focusing on proactive security integration. According to SES Journal Research, organisations are emphasising robust security measures during mobile application development phases to mitigate potential vulnerabilities and enhance forensic readiness before potential investigations even commence. This approach represents a fundamental shift from reactive to preventative digital security strategies.
Key emerging solutions and best practices include:
- Advanced machine learning decryption algorithms
- Standardised forensic data extraction protocols
- Secure hardware-based encryption bypass techniques
- Comprehensive device vulnerability mapping
- Cross-platform forensic compatibility frameworks
- Automated chain of evidence documentation systems
Mastering these emerging approaches requires continuous professional development. Mobile phone forensic examination methods have become essential for forensic professionals seeking to stay ahead of rapidly evolving technological and security landscapes, ensuring they can effectively navigate complex digital investigation challenges.
Overcome the Challenges of Extracting Data from New Mobile Phones
Modern smartphones come with complex encryption, biometric protections and evolving security layers that make digital forensic data extraction daunting. As highlighted in the article, this creates significant hurdles for retrieving evidence while preserving data integrity. If you are facing difficulties navigating these advanced security features or need expert assistance handling encrypted devices, specialist help is essential.
At Computer Forensics Lab, our Forensic Mobile Specialists combine deep technical expertise with cutting-edge tools to expertly recover data from iPhone and Android devices. Our team understands the nuances of hardware encryption, key management and legal constraints that impact mobile forensics. By partnering with us, you gain access to proven strategies that maintain chain of custody and ensure your evidence is legally defensible.
Don’t let technical barriers delay your investigation. Discover how our Mobile Phone Forensic Experts can provide the tailored solutions you need to unlock crucial digital evidence. Visit Computer Forensics Lab today to explore our comprehensive digital forensic investigation services and take the next step towards resolving your most complex mobile data challenges.
Frequently Asked Questions
What is digital forensic data extraction?
Digital forensic data extraction is an investigative process that involves methodically retrieving and analyzing digital evidence from electronic devices while maintaining strict forensic standards.
What challenges do modern mobile operating systems present for data extraction?
Modern mobile operating systems employ advanced security measures, such as file-based encryption and biometric authentication, which complicate traditional data extraction methods.
How can legal regulations affect digital forensic investigations?
Legal regulations specify warrant requirements, protect individual privacy rights, and impose consent protocols, creating nuanced constraints that forensic experts must navigate during data extraction.
What emerging solutions exist for overcoming technical barriers in mobile forensics?
Emerging solutions include advanced machine learning decryption algorithms, standardized forensic data extraction protocols, and secure hardware-based encryption bypass techniques to help forensic professionals address modern security challenges.