A single compromised device can trigger a data breach costing organisations an average of $4.45 million. With stakes this high, understanding each step of a digital forensic investigation is vital for anyone responsible for sensitive information. Whether you work in IT management or cybersecurity, learning the process from initial assessment to supporting legal actions can protect your business and strengthen your response to cyber threats. An IT Forensic Specialist plays a critical role in this process.
Quick Summary
| Key Point | Explanation |
|---|---|
| 1. Assess incidents thoroughly. | Begin by mapping the digital incident to understand its full impact and origin. |
| 2. Preserve evidence meticulously. | Secure devices and create forensically sound copies to maintain data integrity. |
| 3. Conduct comprehensive analysis. | Use advanced techniques to extract and interpret insights from the preserved evidence. |
| 4. Compile clear and detailed reports. | Document findings in a structured manner to support legal and operational needs. |
| 5. Prepare for legal scrutiny. | Ensure all documentation meets regulatory standards for potential legal proceedings. |
Table of Contents
- Step 1: Assess Digital Incident And Scope
- Step 2: Secure Devices And Preserve Evidence
- Step 3: Conduct In-Depth Forensic Analysis
- Step 4: Compile Expert Findings And Reports
- Step 5: Support Legal Or Compliance Proceedings
Step 1: Assess Digital Incident and Scope
In this critical first step, an IT forensic specialist will strategically evaluate the digital incident to understand its complete context and potential damage. Your goal here is comprehensive incident mapping that reveals exactly what happened in your digital environment.
When assessing a digital incident, forensic experts begin by collecting preliminary evidence from multiple sources like computer systems, network logs, mobile devices, and cloud storage. According to digital forensics research, the primary objective is performing forensic collection and initial triage to definitively determine whether a genuine security breach occurred.
The assessment process involves meticulously examining several key dimensions:
- Root cause identification
- Incident timeline reconstruction
- Scope and breadth evaluation
- Potential impact assessment
Your forensic specialist will systematically analyse digital artefacts to trace the incident’s origins and progression. They will hunt for subtle indicators that reveal how the breach started, which systems were compromised, and what potential vulnerabilities were exploited.
Pro Tip: Always preserve original evidence exactly as discovered. Never modify or alter digital forensic materials, as this could compromise the entire investigation.
Once the initial assessment is complete, you will receive a comprehensive report detailing the incident’s forensic profile. This sets the stage for the next critical step: developing a targeted response strategy. Learn more about incident response processes to understand how experts transform initial findings into actionable insights.
Step 2: Secure Devices and Preserve Evidence
In this crucial step, your IT forensic specialist will meticulously secure all digital devices and preserve potential evidence to ensure its legal integrity and admissibility. The goal is to capture and protect digital artefacts without compromising their original state or potential forensic value.
According to digital forensics guidelines, specialists begin by immediately isolating the affected devices from networks and power sources. This prevents potential evidence destruction or further system contamination. As research from governmental cyber security operations indicates, professionals use specialist equipment to capture electronic evidence while maintaining strict compliance with legal investigation requirements.
The evidence preservation process involves several critical techniques:
- Using write blockers to prevent accidental data modification
- Creating forensically sound images of storage media
- Verifying evidence integrity through cryptographic hashing
- Documenting comprehensive chain of custody
Forensic experts employ validated forensic tools that create exact digital replicas of storage devices. These forensic images capture every byte of information without altering the original data something that requires precision and specialised technical expertise.
Pro Tip: Always handle digital devices as potential crime scene evidence. Never attempt personal investigations that might compromise forensic integrity.
Once devices are secured, your forensic specialist will generate detailed documentation tracking every interaction with the evidence.

Step 3: Conduct In-Depth Forensic Analysis
In this critical step, your IT forensic specialist will transform the preserved evidence into meaningful insights by performing a comprehensive and systematic investigation. The objective is to reconstruct the digital incident with precision and uncover the complete narrative hidden within the electronic data.
According to digital forensics research, the analysis process involves multiple sophisticated techniques designed to extract and interpret complex digital artefacts. As insights from cybersecurity experts suggest, forensic professionals use structured models like NIST to methodically examine and analyse digital evidence.
The in-depth forensic analysis encompasses several advanced investigative approaches:
- Memory forensics to capture real-time system state
- Network traffic analysis for communication patterns
- File system examination to track data movements
- Cross drive correlation to identify interconnected evidence
- Hash comparison to validate file authenticity
- Keyword searching for specific contextual information
- Timeline reconstruction of digital events
Forensic experts will meticulously apply file carving techniques to recover deleted or fragmented data that might be crucial to understanding the full incident. They systematically correlate evidence across different devices and platforms to build a comprehensive understanding of what truly occurred.
Pro Tip: Digital forensics is about storytelling through data. Every fragment of evidence potentially holds a critical piece of the investigation puzzle.
Once the detailed analysis is complete, your forensic specialist will prepare a comprehensive report that translates technical findings into clear actionable insights. Explore our guide on forensic data analysis to understand the intricate processes behind digital investigations. The next stage will involve presenting and interpreting these critical findings.
Below is a summary of the core steps in a digital forensic investigation process:
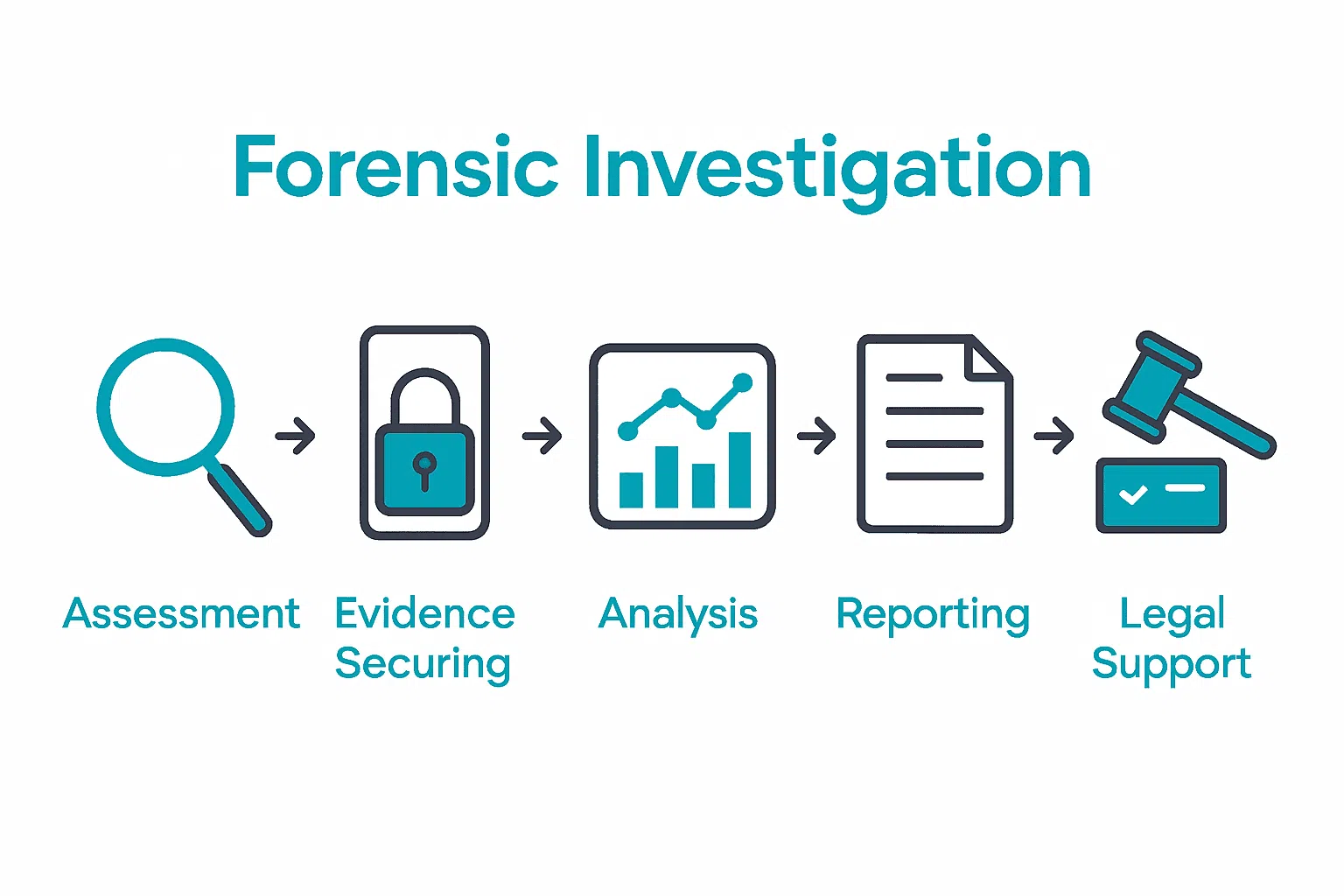
| Step | Primary Objective | Key Activities |
|---|---|---|
| Assess Incident & Scope | Determine incident nature & extent | Evidence collection Timeline reconstruction |
| Secure Devices & Preserve Evidence | Protect data integrity | Device isolation Forensic imaging Chain of custody |
| In-Depth Forensic Analysis | Extract actionable insights | Memory analysis File/system examination |
| Compile Expert Findings | Create clear, authoritative reports | Methodology explanation Incident reconstruction |
| Support Legal Proceedings | Ensure legal admissibility | Expert statements Regulatory compliance |
Step 4: Compile Expert Findings and Reports
In this pivotal stage, your IT forensic specialist transforms complex technical investigations into clear, authoritative documentation that can withstand legal and professional scrutiny. The goal is to create a comprehensive narrative that communicates technical findings in a manner accessible to legal professionals, management, and other stakeholders.
According to forensic documentation standards, these reports must be meticulously structured to meet rigorous professional guidelines. As research indicates, forensic specialists produce controlled reports aligned with international standards such as ISO 17025 to ensure absolute credibility and precision.
The report compilation process involves several critical components:
- Detailed methodology explanation
- Chronological incident reconstruction
- Evidence inventory and authentication
- Technical analysis summaries
- Clear conclusions and potential implications
- Recommendations for future prevention
Forensic experts craft these documents with extraordinary attention to detail. Each report serves as an official record that can potentially be used in legal proceedings, internal investigations, or cybersecurity improvement strategies. The language must be simultaneously technical and comprehensible, bridging the gap between complex digital forensics and practical understanding.
Pro Tip: Treat every forensic report as potential legal evidence. Clarity, objectivity, and precision are paramount.
Once compiled, the report becomes your strategic document for understanding the digital incident and planning future protective measures. Explore our guide on digital forensic investigations to gain deeper insights into professional reporting standards. The next stage involves presenting these findings to key stakeholders and determining subsequent actions.
Step 5: Support Legal or Compliance Proceedings
In this critical final stage, your IT forensic specialist transforms technical investigations into legally admissible evidence that meets stringent regulatory standards. The objective is to prepare documentation that can withstand intense legal scrutiny and support your organisational or legal requirements.
According to legal precedents, electronic evidence is only accepted when collection meticulously complies with current technical standards. As research from landmark cases like Gates Rubber Co. v. Bando demonstrates, forensic documentation must follow rigorous acquisition protocols to maintain legal admissibility.
Supporting legal proceedings involves several strategic components:
- Preparing expert witness statements
- Ensuring chain of evidence preservation
- Documenting forensic methodologies
- Translating technical findings for legal comprehension
- Meeting regulatory compliance requirements
- Supporting breach reporting obligations
Forensic specialists understand that every document could potentially become critical evidence in court. They craft reports that not only explain technical findings but also provide clear narratives that legal professionals can understand and leverage.
Pro Tip: Treat every forensic report as if it will be examined under a microscope in a courtroom. Precision is your most powerful ally.
Once the legal support documentation is complete, you will have a comprehensive package ready for potential litigation or regulatory review. Learn more about digital forensics in litigation to understand the intricate process of transforming technical findings into legal strategy. This final step ensures your digital investigation is thoroughly documented and legally defensible.
Take Charge of Your Cyber Incident with Leading IT Forensic Expertise
When facing a sudden digital breach or data loss, the uncertainty can be overwhelming. The article outlined the critical role of an IT forensic specialist in assessing incidents, securing evidence, and delivering actionable findings that stand up in legal or compliance settings. You need reliable, expert support when handling issues like data breaches, employee misconduct or intellectual property theft. Any misstep in evidence handling can compromise legal outcomes or worsen the damage.
At Computer Forensics Lab, our specialists use the same proven steps and advanced techniques described in the article. We go further by offering targeted support for complex hacking cases through our Hacking Investigation and Computer Hacking Examination services. Do not risk further loss or uncertainty. Secure a professional assessment and protect your position by contacting our team today at https://computerforensicslab.co.uk. Take the next step towards clarity and resolution now.
Frequently Asked Questions
How can an IT forensic specialist help assess a digital incident?
An IT forensic specialist helps assess a digital incident by collecting evidence and mapping out the incident’s timeline. They analyze various data sources to identify the root cause and potential impact, providing clarity on what occurred in your environment.
What steps does an IT forensic specialist take to secure devices during an investigation?
To secure devices, an IT forensic specialist isolates affected devices from networks and power sources to prevent further contamination. They use specialized tools to create forensically sound images of storage media, ensuring that the original data’s integrity is maintained.
What techniques are used in in-depth forensic analysis?
In-depth forensic analysis involves techniques such as memory forensics, network traffic analysis, and file system examination. These methods help reconstruct the incident’s narrative and extract valuable insights from preserved evidence.
How are expert findings documented in an IT forensic investigation?
Expert findings are documented by creating a clear, comprehensive report detailing methodologies, incident chronologies, and evidence summaries. This report serves as a strategic document for understanding the incident and communicates findings in a way that is accessible to stakeholders.
Why is legal support important in a digital forensic investigation?
Legal support is crucial because it ensures that documentation meets regulatory standards and can withstand legal scrutiny. Proper preparation of expert witness statements and maintaining the chain of evidence are essential to defend against potential legal challenges.
