Most organisations underestimate how complex digital investigations have become, yet even seasoned British experts are now facing sophisticated threats that demand advanced forensic skills. With cyber attacks increasing globally, the ability to collect and preserve digital evidence is not just for law enforcement but for every company seeking protection. This article sheds light on the fundamentals of cybersecurity forensics, sharing why over 80 percent of modern investigations hinge on specialised digital evidence procedures and how these practices help safeguard both legal and technological interests.
Table of Contents
- Defining Forensics In Cybersecurity Practice
- Types Of Digital Forensics In Cybersecurity
- How Digital Forensics Investigations Work
- Legal Duties And Chain Of Custody
- Risks, Limitations, And Best Practices
Key Takeaways
| Point | Details |
|---|---|
| Importance of Digital Forensics | Digital forensics bridges technology and law, playing a critical role in investigations by recovering and preserving evidence to support legal proceedings. |
| Stages of Forensic Investigations | Successful investigations follow systematic stages including identification, preservation, and analysis, ensuring that evidence remains intact and legally admissible. |
| Legal Responsibilities | Forensic professionals must adhere to strict legal protocols to maintain the integrity and traceability of digital evidence throughout the investigation process. |
| Risk Management in Digital Forensics | To navigate evolving technological challenges, professionals should engage in continuous training and adopt adaptive methodologies for effective evidence handling. |
Defining Forensics in Cybersecurity Practice
Cybersecurity forensics represents a sophisticated discipline bridging technological investigation and legal evidence collection. At its core, this practice involves systematically recovering, examining, and preserving digital information that can substantiate criminal activities, corporate misconduct, or potential security breaches.
Digital forensics plays a crucial role in law enforcement by providing investigators with advanced tools and strategies to collect and analyse digital evidence. Professionals in this field employ specialised techniques to recover deleted files, trace complex internet activities, and pinpoint the precise origins of cyber attacks. These investigations require meticulous attention to detail, ensuring that all recovered data maintains its legal integrity and can withstand rigorous judicial scrutiny.
The forensic process encompasses several critical stages that transform raw digital data into admissible evidence. These stages typically include evidence acquisition, preservation, analysis, and documentation. Forensic experts must maintain strict chain of custody protocols, ensuring that digital artefacts are collected, stored, and processed without contamination or alterations that might compromise their evidentiary value.
Digital Evidence Collection Methods:
- Forensic imaging of storage devices
- Network traffic analysis
- Metadata extraction
- Browser and application log examination
- Encrypted data decryption
Expert Tip: Maintain precise documentation during every stage of digital evidence collection, creating a comprehensive audit trail that validates the forensic investigation’s scientific and legal credibility.
By integrating technological expertise with legal standards, cybersecurity forensics provides a critical mechanism for uncovering digital truth in an increasingly complex technological landscape.
Types of Digital Forensics in Cybersecurity
Digital forensics encompasses a wide range of specialised investigative techniques designed to extract, analyse, and preserve electronic evidence across diverse technological environments. These methodologies are critical for uncovering digital insights that can support legal proceedings, cybersecurity investigations, and organisational security assessments.
Modern digital forensics has evolved to address the complexities of various technological platforms. Mobile forensics and cloud forensics represent two critical subspecialties that tackle the intricate challenges of contemporary digital investigations. Mobile forensics focuses on extracting and analysing data from smartphones, tablets, and other portable devices, while cloud forensics addresses the unique challenges of investigating evidence stored across decentralized cloud infrastructures.
The primary categories of digital forensics include:
Key Digital Forensics Domains:
- Computer Forensics: Investigating desktop and laptop systems
- Network Forensics: Analysing network traffic and communication logs
- Mobile Forensics: Examining smartphone and portable device data
- Cloud Forensics: Investigating distributed cloud storage systems
- Database Forensics: Exploring database management systems and records
- Malware Forensics: Analysing malicious software and its potential impacts
- Email Forensics: Investigating electronic communication records
Each forensic domain requires specialized tools, methodologies, and expert knowledge to effectively recover and interpret digital evidence. Forensic techniques have become increasingly sophisticated in responding to the rapidly evolving landscape of digital technologies and cybersecurity threats.
Here is a comparison of key digital forensics domains and their primary focus areas:
| Forensics Domain | Main Objective | Example of Evidence Analysed |
|---|---|---|
| Computer Forensics | Investigate computers/desktops | Hard drives, system logs |
| Network Forensics | Analyse network communications | Packet captures, traffic logs |
| Mobile Forensics | Examine portable smart devices | SMS, call logs, app data |
| Cloud Forensics | Investigate cloud infrastructure | Virtual drives, cloud access records |
| Database Forensics | Explore databases and records | Table histories, query logs |
| Malware Forensics | Analyse malicious software | Virus signatures, payload behaviour |
| Email Forensics | Investigate email communications | Email headers, attachments, metadata |
Pro Tip: Always maintain strict chain of custody protocols when handling digital evidence, ensuring that forensic investigations remain legally admissible and scientifically rigorous.
By understanding these diverse forensic approaches, legal professionals, cybersecurity experts, and investigators can effectively navigate the complex digital landscape and uncover critical evidence hidden within technological systems.
How Digital Forensics Investigations Work
Digital forensics investigations represent a meticulous and structured approach to uncovering digital evidence, requiring precision, technical expertise, and rigorous methodological standards. These investigations serve as critical mechanisms for understanding complex technological incidents, supporting legal proceedings, and revealing hidden digital narratives.
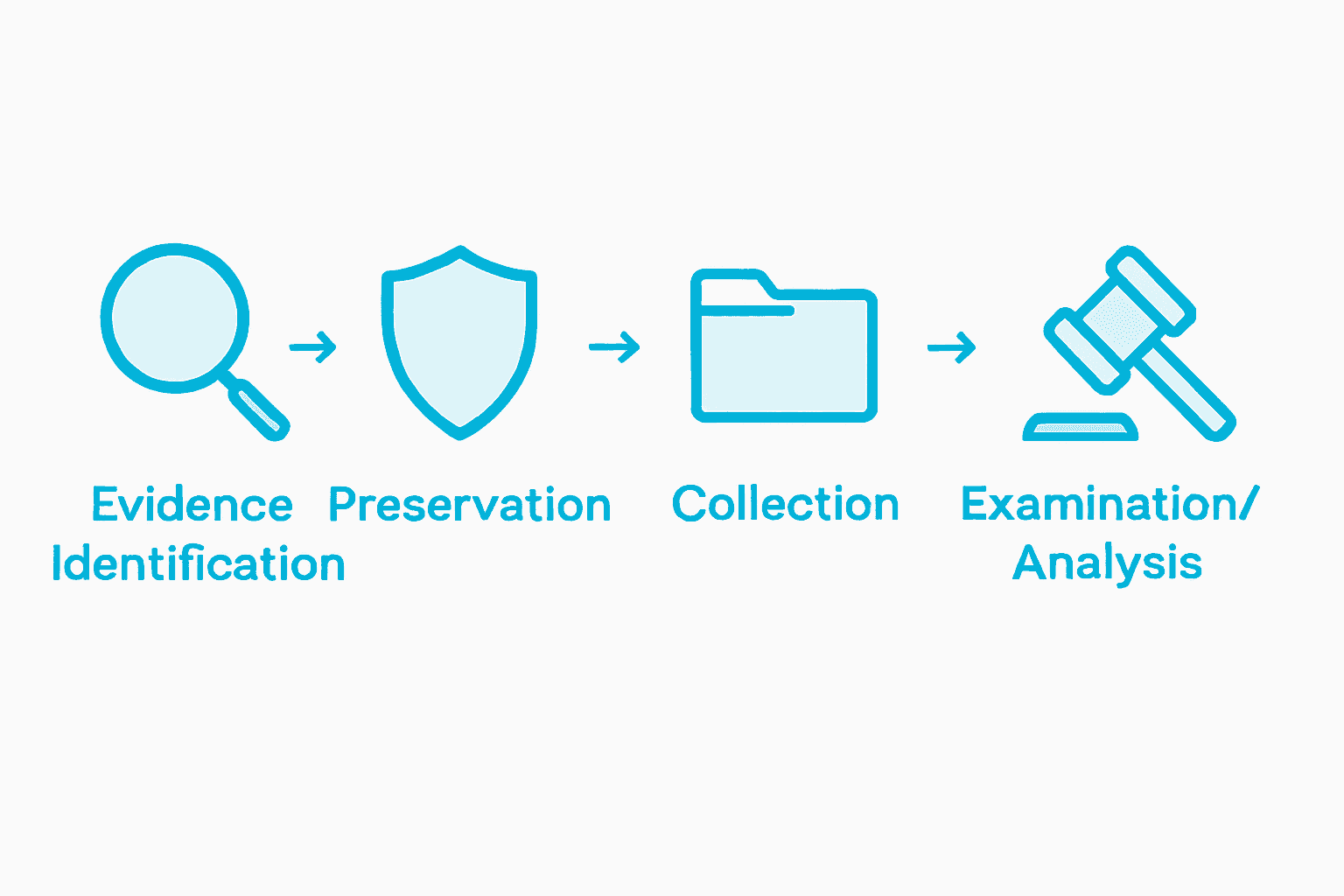
Digital forensics investigations encompass systematic stages that transform raw technological data into legally admissible evidence. These stages typically include identification, preservation, analysis, and presentation, each designed to maintain the integrity and authenticity of digital artifacts while extracting meaningful insights.
Key Investigation Stages:
- Identification: Determining potential sources of digital evidence
- Preservation: Securing and protecting digital artifacts from contamination
- Collection: Carefully extracting digital evidence using forensically sound methods
- Examination: Detailed analysis of collected digital materials
- Analysis: Interpreting collected evidence and establishing contextual relationships
- Reporting: Documenting findings in a comprehensive, legally defensible manner
Forensic investigators employ sophisticated tools and techniques to navigate complex digital landscapes. Advanced computer forensics workflows enable professionals to recover deleted files, trace digital communications, and reconstruct intricate technological timelines with remarkable precision.
Pro Tip: Document every step of your digital forensics investigation meticulously, ensuring each action is repeatable and defensible under legal scrutiny.
By understanding these systematic approaches, legal professionals and cybersecurity experts can effectively unravel complex digital mysteries and transform technological evidence into compelling narratives of truth.
Legal Duties and Chain of Custody
Digital forensics operates within a complex legal framework that demands absolute precision, transparency, and adherence to stringent professional standards. Forensic professionals must navigate intricate legal responsibilities while maintaining the integrity of digital evidence throughout every stage of investigation.
Legal duties in digital forensics encompass critical protocols for evidence collection, preservation, and analysis that directly impact the credibility of potential court proceedings. These responsibilities require forensic experts to document every action meticulously, ensuring that digital evidence remains uncontaminated and legally admissible.
Key Legal Responsibilities:
- Preservation: Maintaining original evidence in pristine condition
- Documentation: Recording comprehensive details of evidence handling
- Integrity: Preventing unauthorized modifications
- Traceability: Establishing clear accountability for evidence movement
- Confidentiality: Protecting sensitive information during investigations
Comprehensive chain of custody procedures are fundamental to maintaining legal standards. These protocols require forensic professionals to create detailed logs tracking every interaction with digital evidence, including timestamps, personnel involved, and specific actions taken during the investigation.
Pro Tip: Create a rigorous, contemporaneous documentation system that records each evidence interaction with precision, including who handled the evidence, when, and under what circumstances.
By understanding and implementing these legal duties, forensic professionals safeguard the reliability and admissibility of digital evidence, ensuring that technological investigations can withstand the most stringent legal scrutiny.
Risks, Limitations, and Best Practices
Digital forensics represents a complex and evolving discipline fraught with technological challenges and regulatory complexities. Forensic professionals must navigate an increasingly sophisticated landscape of cybersecurity threats, legal requirements, and technological limitations that demand continuous adaptation and strategic thinking.
Enterprises face escalating cybersecurity challenges that necessitate robust risk mitigation strategies, including proactive threat anticipation and comprehensive forensic investigation protocols. These strategies must align with stringent regulatory frameworks such as GDPR and CCPA, ensuring that digital evidence collection methods remain legally compliant and forensically sound.
Critical Risk Management Strategies:
- Technological Volatility: Addressing rapid technological changes
- Evidence Preservation: Maintaining digital artifact integrity
- Regulatory Compliance: Adhering to international legal standards
- Privacy Protection: Safeguarding sensitive information
- Continuous Training: Updating skills and methodologies
Forensic visualization techniques offer innovative approaches to addressing traditional investigative limitations, enabling security analysts to identify and analyse complex cyber threats more effectively. These advanced methodological approaches help professionals overcome conventional investigative constraints by providing enhanced visual representation of digital evidence.
Pro Tip: Develop a comprehensive, adaptive forensic methodology that anticipates technological shifts and integrates continuous learning and skill development.
By understanding and proactively managing these risks, forensic professionals can transform potential limitations into strategic opportunities for more sophisticated digital investigations.
Below is a summary of common risks in digital forensics alongside best practice responses:
| Risk Area | Risk Example | Best Practice Response |
|---|---|---|
| Technological Volatility | New encryption obscures data | Invest in continuous tool updates |
| Evidence Preservation | Contamination of artefacts | Follow strict chain-of-custody protocols |
| Regulatory Compliance | GDPR violations | Align practices with latest legal standards |
| Privacy Protection | Data exposure in investigations | Minimise data access and use encryption |
| Skills Obsolescence | Outdated forensic techniques | Regular and comprehensive skills training |
Protect Your Digital Evidence with Expert Cybersecurity Forensics Support
In a world where safeguarding digital evidence is critical to uncovering truth and supporting legal cases, challenges like maintaining the chain of custody and using advanced forensic techniques demand trusted expertise. If you are facing risks related to data breaches, cybercrime investigations, or employee misconduct, it is essential to partner with specialists who understand the complexities of digital forensic science.
Computer Forensics Lab offers comprehensive services tailored to your needs, including secure data recovery, malware analysis, and expert witness reporting. Explore the full range of solutions in Forensic Science and specialised insights on Hacking Investigation to empower your cybersecurity strategy. Don’t wait until digital evidence is lost or compromised. Visit Computer Forensics Lab now to protect your interests and ensure your investigations meet the highest legal and technical standards.
Frequently Asked Questions
What is cybersecurity forensics?
Cybersecurity forensics is the discipline that involves recovering, examining, and preserving digital information to substantiate criminal activities, corporate misconduct, or security breaches. It employs various techniques to uncover and analyse digital evidence.
What are the primary stages of a digital forensics investigation?
The main stages of a digital forensics investigation include identification, preservation, collection, examination, analysis, and reporting. Each stage is critical for maintaining the integrity and authenticity of the digital evidence collected.
What types of digital forensics exist?
Key types of digital forensics include computer forensics, network forensics, mobile forensics, cloud forensics, database forensics, malware forensics, and email forensics. Each type focuses on different sources of digital evidence and requires specialised techniques.
Why is maintaining a chain of custody important in digital forensics?
Maintaining a chain of custody is crucial to ensure the legal integrity of digital evidence. It involves documenting every interaction with the evidence, preventing contamination, and establishing clear accountability to make certain that the evidence is admissible in court.
Recommended
- Role of Digital Evidence – Impact on Modern Investigations
- Step by Step Digital Evidence Collection Guide
- How to Identify Cybercrime Evidence Step by Step
- 7 Top Digital Forensics Techniques Every Legal Team Must Know
- Confidential Waste Risk Management: Essential Guide for UK Businesses 2025 – Venture Waste