Most people are surprised to learn that over 90 percent of lost digital data can be recovered with the right forensic methods. As technology shapes how evidence is gathered, British specialists play a vital role in ensuring digital information stays secure and reliable. Understanding data recovery in digital forensics helps you grasp what happens when files go missing or become evidence, offering a clear look at the techniques that keep information admissible in court.
Table of Contents
- Defining Data Recovery In Digital Forensics
- Types Of Data Loss And Recovery Methods
- How Digital Evidence Is Recovered Safely
- Legal Standards And Evidence Admissibility
- Risks, Limits, And Common Mistakes
Key Takeaways
| Point | Details |
|---|---|
| Data Recovery in Digital Forensics | The process involves retrieving and preserving electronic data when standard methods fail, requiring advanced techniques to maintain evidential integrity. |
| Types of Data Loss | Professionals must utilise distinct recovery methods, including logical, physical, cloud, and network data recovery, tailored to specific scenarios. |
| Importance of Documentation | Maintaining detailed logs of recovery steps and conditions is crucial for evidential admissibility and forensic transparency. |
| Risks and Best Practices | Improper handling of evidence can render it inadmissible; therefore, using write-blockers and timely interventions are essential for successful data recovery. |
Defining Data Recovery In Digital Forensics
Data recovery in digital forensics represents the sophisticated process of retrieving, preserving, and analysing electronic data from various storage media when standard access methods fail. At its core, this discipline involves extracting digital evidence from devices under suspicion, ensuring critical information remains intact and admissible in legal proceedings.
Forensic data recovery encompasses a structured methodology that goes far beyond simple file retrieval. Digital forensics professionals employ advanced techniques to recuperate deleted, formatted, corrupted, or damaged data from complex storage systems. These methods include fragment forensics, which involves reconstructing digital evidence from partial file remnants, and sophisticated recovery strategies designed to maintain the evidential integrity of electronic records.
The technical complexity of data recovery demands specialised knowledge and precision. Investigators must navigate intricate challenges such as encrypted storage, damaged hardware, and intentionally obscured digital traces. Cyber forensics techniques are particularly critical in scenarios involving Android phone forensics, where data extraction requires deep technical expertise and specialised tools to bypass security mechanisms and recover potentially crucial evidence.
Pro Tip: Preserve Digital Evidence: Always create a forensic image of the original storage device before attempting any data recovery to maintain the chain of custody and prevent potential contamination of evidence.
Types Of Data Loss And Recovery Methods
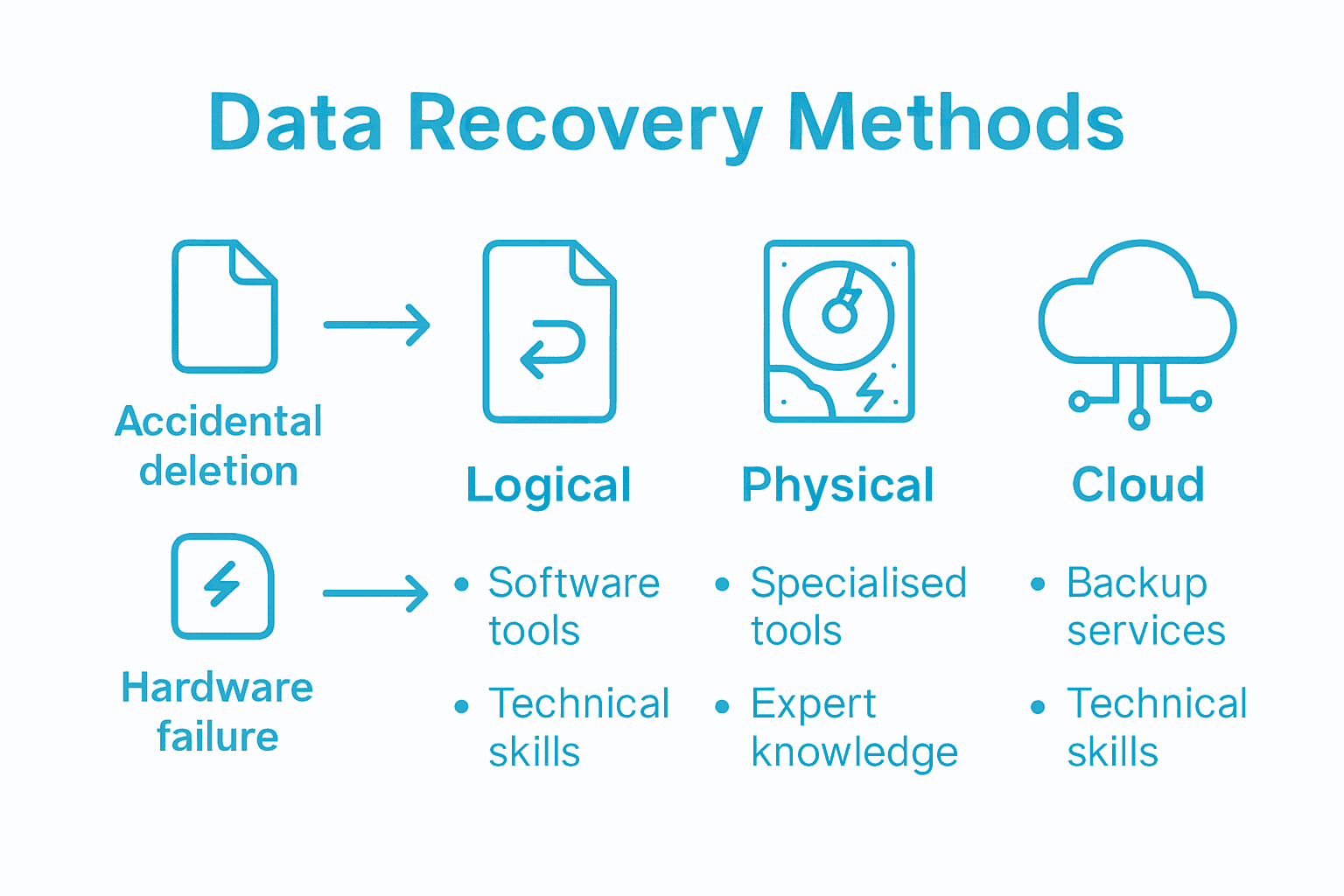
Digital forensics professionals encounter multiple categories of data loss, each requiring specific recovery strategies tailored to unique technological challenges. Four primary types of data recovery techniques exist: logical data recovery, physical data recovery, cloud data recovery, and remote/network data recovery, each addressing distinct scenarios of electronic information retrieval.
Logical Data Recovery addresses software-related data loss scenarios, such as accidental file deletion, system crashes, or corrupted file systems. This method involves sophisticated software techniques that reconstruct digital information without physically manipulating storage devices. Investigators use specialised algorithms to scan storage media, identifying and recovering fragmented or hidden data traces that standard operating systems cannot access.
Physical Data Recovery becomes critical when storage media experience hardware failures, such as mechanical hard drive damage, electrical component malfunctions, or severe physical trauma. These complex recovery processes require clean room environments, specialised equipment, and advanced forensic techniques to extract data from damaged storage systems. Standardised classification and authentication protocols are essential in ensuring the integrity of recovered file systems, particularly when the evidence might be presented in legal proceedings.
Cloud and Network Data Recovery represent increasingly sophisticated domains in digital forensics. These methods address data retrieval from distributed storage systems, requiring expertise in navigating complex network architectures, understanding cloud storage mechanisms, and implementing advanced decryption and reconstruction techniques. Forensic professionals must possess deep technical knowledge to navigate the intricate layers of cloud infrastructure and remote storage environments.
Pro Tip: Systematic Documentation: Always maintain a detailed log of every recovery step, including initial device conditions, recovery methods employed, and recovered data characteristics to ensure forensic transparency and evidential admissibility.
Here is a comparison of the main data recovery methods used in digital forensics:
| Method | Typical Scenario | Required Expertise | Common Tools/Techniques |
|---|---|---|---|
| Logical Data Recovery | Deleted or corrupted files | Advanced software skills | File carving, data scanners |
| Physical Data Recovery | Damaged or faulty hardware | Clean room, hardware repair | Disk imaging, chip-off recovery |
| Cloud Data Recovery | Data on remote/cloud platforms | Cloud infrastructure knowledge | API analysis, log extraction |
| Network Data Recovery | Data lost in networked systems | Network forensic analysis | Packet capture, traffic analysis |
How Digital Evidence Is Recovered Safely
Digital evidence recovery requires meticulous attention to safety protocols and cutting-edge technological approaches to ensure the preservation and integrity of electronic information. Forensic laboratories employ specialised tools and techniques for safely extracting data from complex storage technologies, particularly when dealing with advanced storage media like NAND flash memories that demand sophisticated extraction methodologies.
The safety of digital evidence recovery hinges on maintaining strict chain of custody and implementing robust forensic protocols. Investigators must create exact forensic duplicates of storage devices, ensuring that no alterations occur during the investigation process. This requires sophisticated write-blocking technologies, forensically validated imaging tools, and comprehensive documentation of every step undertaken during the evidence collection and analysis phases.
Emerging blockchain-based forensic frameworks are revolutionising the approach to secure digital evidence preservation, introducing unprecedented levels of provenance tracking and data integrity verification. These advanced systems enable forensic professionals to trace data origins, maintain immutable records, and expedite the process of evidence extraction while maintaining the highest standards of digital forensic integrity. The ability to create verifiable, tamper-evident records represents a significant leap forward in ensuring the admissibility and reliability of digital evidence in legal proceedings.
Technical forensic teams must constantly update their methodologies and tools to address the rapidly evolving landscape of digital storage technologies. This requires continuous training, investment in state-of-the-art forensic software and hardware, and a commitment to maintaining the highest standards of scientific and legal precision in digital evidence recovery.
Pro Tip: Evidence Preservation: Always create multiple forensic images of digital storage devices and store them in secure, write-protected environments to prevent accidental modification and maintain multiple independent verification points.
Legal Standards And Evidence Admissibility
Digital forensic evidence represents a critical component of modern legal proceedings, requiring stringent standards to ensure its reliability and admissibility in court. Sophisticated frameworks have emerged to model and analyse digital forensic knowledge, providing structured approaches that enhance the credibility and scientific integrity of electronic evidence collection and presentation.
The legal admissibility of digital evidence hinges on several fundamental principles. Forensic investigators must demonstrate a clear and unbroken chain of custody, proving that the evidence has not been tampered with or altered during collection and analysis. This requires meticulous documentation, forensically sound imaging techniques, and the ability to reproduce exactly how digital artifacts were extracted and preserved. Courts demand rigorous verification processes that can withstand intense scrutiny and challenge.
Emerging research addresses complex challenges in proving data possession, particularly in cloud storage environments, developing innovative methodologies for establishing the authenticity and origin of digital evidence. These advanced techniques provide legal professionals with robust mechanisms to validate electronic information, ensuring that digital evidence meets the stringent requirements of judicial review. The complexity of modern digital storage systems demands increasingly sophisticated forensic approaches that can conclusively demonstrate the integrity and provenance of electronic records.
Legal standards for digital evidence continue to evolve, reflecting the rapid technological advancements in data storage and retrieval. Expert witnesses must possess not only technical expertise but also the ability to communicate complex forensic methodologies in a manner comprehensible to legal professionals and jurors. This requires a delicate balance between technical precision and clear, accessible explanation of digital forensic processes.
Pro Tip: Evidence Authentication: Maintain comprehensive, timestamped logs of all forensic procedures, including detailed metadata about evidence collection, to provide irrefutable documentation of the evidence’s origin and handling.
Risks, Limits, And Common Mistakes
Digital forensic investigations involve numerous potential pitfalls that can compromise the integrity and reliability of electronic evidence. Challenges in timeline-based event reconstruction highlight the complexity of forensic data analysis, revealing significant risks associated with fragmented research approaches and massive data volumes that can obscure critical investigative insights.
One of the most prevalent risks in digital forensics is improper evidence handling. Investigators must recognise that every interaction with digital storage media carries the potential to alter or contaminate evidence. Fundamental mistakes often include failing to create forensic write-blocks, using non-validated tools, or allowing unauthorized personnel to access potential evidence. These errors can render critical digital artifacts inadmissible in legal proceedings, effectively destroying the evidentiary value of potentially crucial electronic information.
Data recovery and undeletion processes are not foolproof techniques, presenting significant limitations that forensic professionals must understand. The success of data retrieval depends critically on the timeliness of intervention, with the probability of successful recovery diminishing rapidly as time passes and additional system interactions occur. Each write operation to a storage device increases the likelihood of permanent data loss, making immediate and precise forensic intervention paramount.
Technical limitations compound the risks inherent in digital forensics. Encryption technologies, cloud storage complexities, and rapidly evolving digital platforms create substantial challenges for forensic investigators. Modern storage systems employ increasingly sophisticated data protection mechanisms that can render traditional recovery techniques ineffective, requiring continuous adaptation of forensic methodologies and tools.
Pro Tip: Preservation Protocol: Always create immediate forensic images of digital storage devices using write-blocked hardware, and document every step of the evidence acquisition process to maintain chain of custody and maximize potential data recovery.
The following table summarises key risks and mistakes in digital evidence recovery:
| Risk Area | Potential Impact | Preventative Measure |
|---|---|---|
| Improper Handling | Evidence may become inadmissible | Use write-blockers and limit access |
| Delayed Response | Permanent loss of data possible | Initiate recovery at first opportunity |
| Inadequate Documentation | Weakens legal chain of custody | Maintain detailed and timestamped logs |
| Outdated Tools | Evidence may be unrecoverable | Regularly update software and hardware |
Expert Forensic Data Recovery Solutions Tailored to Your Needs
Data recovery in digital forensics can be a complex challenge requiring precision and specialised knowledge. Whether you face issues like corrupted files, damaged hardware, or cloud data retrieval, understanding best practices is essential to preserve the integrity of your digital evidence. At Computer Forensics Lab, we recognise the critical importance of creating forensic images, maintaining chain of custody, and applying advanced techniques while avoiding common pitfalls such as improper handling or delayed response.
Take control of your digital investigation with our team of Forensic Data Specialists and cutting-edge Forensic Data Recovery services. Our London-based experts work closely with legal professionals, law enforcement, and businesses to ensure your recovered data withstands legal scrutiny. Do not let vital electronic evidence slip away due to inadequate processes. Visit Computer Forensics Lab today to secure professional assistance from industry leaders and achieve reliable, court-ready results.
Frequently Asked Questions
What is data recovery in digital forensics?
Data recovery in digital forensics is the process of retrieving, preserving, and analysing electronic data from storage media when normal access fails. It aims to extract critical digital evidence while maintaining its integrity for legal proceedings.
What are the main types of data recovery methods used in digital forensics?
The main types of data recovery methods include logical data recovery, which addresses software-related data loss; physical data recovery for hardware failures; cloud data recovery, which pertains to remote storage systems; and network data recovery for data lost within networked systems.
How can digital evidence be recovered safely?
Digital evidence can be recovered safely by maintaining a strict chain of custody, creating exact forensic duplicates of storage devices, utilising write-blocking technologies, and documenting every step undertaken during evidence collection and analysis.
What are some common mistakes in digital forensic investigations?
Common mistakes in digital forensic investigations include improper evidence handling, delayed response to data loss, inadequate documentation of the recovery process, and the use of outdated tools which can compromise the integrity of the evidence.