Nearly every digital forensic specialist faces the challenge of preserving evidence that truly stands up in court. Digital investigations demand more than technical know how. They require careful legal groundwork and flawless documentation that follows strict procedures. Getting these steps right means your results remain credible and your process passes legal scrutiny. Discover every crucial stage of a digital forensic investigation that ensures your evidence holds up when it matters most.
Table of Contents
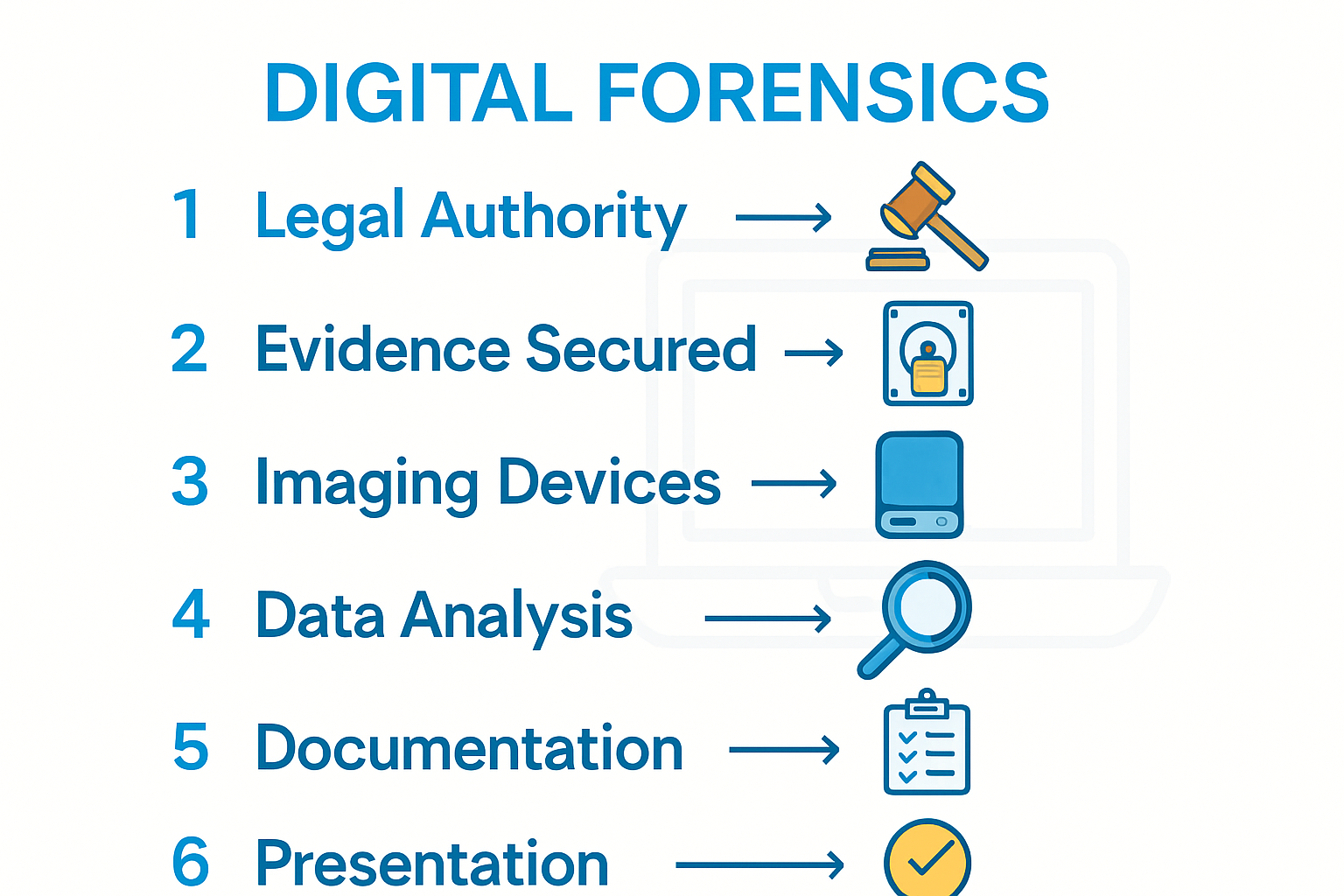
- Establish Legal Authority And Prepare Equipment
- Identify And Secure Relevant Digital Evidence
- Acquire Forensic Images Of Target Devices
- Analyse Collected Data Using Forensic Tools
- Document Findings And Maintain Chain Of Custody
- Present Results And Verify Evidence Integrity
Quick Summary
| Important Insight | Detailed Explanation |
|---|---|
| 1. Establish Legal Authority First | Obtain necessary legal permissions such as warrants or consent before accessing digital devices to ensure evidence is admissible in court. |
| 2. Prepare Investigative Equipment Thoroughly | Equip yourself with write blockers, forensic software, and evidence collection tools to maintain the integrity of the digital evidence. |
| 3. Systematically Identify and Secure Evidence | Methodically locate and preserve digital evidence, creating forensic images while documenting every step to ensure chain of custody. |
| 4. Conduct In-Depth Forensic Analysis | Use specialised software to analyse digital evidence for hidden patterns or deleted data, maintaining detailed documentation throughout the process. |
| 5. Present Findings with Clarity and Integrity | Create a comprehensive report that details methodologies and findings, ensuring to verify evidence integrity and maintain clear chain of custody documentation. |
Stage 1: Establish legal authority and prepare equipment
Before diving into digital forensics, you’ll need to establish robust legal authority and carefully prepare your investigative equipment. This critical first step ensures that any evidence you collect will be admissible in legal proceedings and protects the integrity of your investigation.
Navigating the legal landscape requires understanding specific consent requirements for digital searches. You must obtain proper authorisation through warrants, explicit consent, or organisational policies before accessing any digital systems or devices.
Equipment preparation is equally paramount. Your forensic toolkit should include write blockers, forensic workstations, evidence collection drives, and specialised software that prevents any accidental data modification. Always document every piece of equipment used, its serial number, and its forensic configuration to maintain a clear chain of custody. A pro tip: create a detailed equipment log before starting any investigation, which will serve as crucial documentation if your findings are challenged in court.
Once your legal groundwork is established and equipment is meticulously prepared, you’re ready to move forward to the next phase of your digital forensic investigation.
Stage 2: Identify and secure relevant digital evidence
In this critical stage of digital forensics, you’ll systematically locate and preserve potential sources of digital evidence without compromising their integrity. Your primary goal is to identify and secure digital artefacts that might contain crucial information related to the investigation.
The process begins with a comprehensive systematic approach to identifying digital evidence sources. This means meticulously examining all potential digital devices and storage media, including computers, mobile phones, external drives, cloud storage, and network logs. Look beyond obvious sources by considering metadata, system logs, email archives, and even seemingly innocuous files that might contain hidden traces of digital activity.
Securing evidence requires precision and careful documentation. You must create forensic images of all digital media using write blockers to prevent any accidental data modification. Implement rigorous documentation protocols that record every action, including device serial numbers, hash values, and precise collection timestamps. This creates an unbreakable chain of custody that will withstand legal scrutiny.
Pro tip: Always work on forensic copies, never the original evidence. This ensures that the original data remains pristine and untouched, maintaining its legal admissibility. Your next step involves carefully analysing these secured digital artefacts to extract meaningful investigative insights.
Étape 3: Acquire forensic images of target devices
In this crucial stage of digital forensics, you’ll create precise forensic images of target devices that capture every digital fragment without altering the original data. Your objective is to generate bit-by-bit exact copies that preserve the complete digital landscape of each device for meticulous investigation.
The acquisition process demands scientifically derived methods for preserving digital evidence. Start by selecting appropriate forensic imaging tools that support comprehensive bit-stream copying. Ensure you use write blockers to prevent any inadvertent data modification during the imaging process. Each device requires a unique approach whether you’re dealing with hard drives, mobile phones, or cloud storage repositories.
Documentation is paramount in this stage. Maintain rigorous communication and documentation protocols that record every technical detail of the acquisition. Generate cryptographic hash values MD5 or SHA256 for each forensic image to validate its integrity and prove no data tampering occurred. Pro tip: Always create multiple verified copies stored in secure, separate locations to protect against potential media failure.
With your forensic images securely captured and documented, you are now prepared to move into the next phase of detailed digital evidence analysis.
Étape 4: Analyse collected data using forensic tools
In this critical phase of digital forensics, you’ll transform raw digital images into meaningful investigative insights by systematically examining every digital fragment using specialised forensic analysis tools. Your goal is to uncover hidden patterns, recover deleted information, and reconstruct the digital narrative hidden within the collected evidence.
The analysis process demands meticulous methodologies for interpreting digital evidence. Begin by selecting comprehensive forensic software capable of deep file system analysis, metadata extraction, and advanced data carving techniques. Scrutinise each digital artifact for timestamps, user activity logs, internet browsing history, communication records, and potential hidden or encrypted data. Your forensic tools should allow granular exploration of file systems, slack spaces, and unallocated disk sectors where crucial evidence might reside.
Remember that digital forensic analysis is an iterative process requiring multiple examination cycles to support investigative hypotheses. Cross-reference findings across different tools and platforms to validate your observations. Pro tip: Always maintain a detailed log of every analysis step, tool used, and configuration settings to ensure your findings can withstand rigorous legal and technical scrutiny.
With your forensic analysis complete, you are now prepared to compile your findings into a comprehensive report that will serve as a critical piece of evidence in your investigation.
Stage 5: Document findings and maintain chain of custody
In this pivotal stage of digital forensics, you’ll transform your investigative insights into a comprehensive, legally defensible documentation that meticulously tracks every aspect of evidence handling. Your goal is to create a detailed record that demonstrates the integrity and authenticity of your forensic investigation from start to finish.
Permanent documentation of investigative information serves multiple critical purposes. Begin by creating a chronological log that records each investigative action, including device acquisition timestamps, analysis methods, tools used, and specific findings. Ensure your documentation includes precise details about the location, condition, and status of each electronic device examined. This comprehensive approach provides decision makers and legal authorities with a transparent and verifiable account of your investigative process.
Understanding legal procedures and ethical boundaries is fundamental to maintaining a robust chain of custody. Every piece of digital evidence must be tracked with meticulous care, recording who handled the evidence, when, and under what circumstances. Create a detailed evidence custody log that includes signature timestamps, transfer protocols, and storage conditions. Pro tip: Use tamper evident seals and digital signatures to provide additional layers of authentication for your forensic documentation.
With your findings thoroughly documented and chain of custody rigorously maintained, you are now prepared to present your forensic report with confidence and professional credibility.
Étape 6: Present results and verify evidence integrity
In this final stage of digital forensics, you’ll transform your meticulous investigation into a compelling narrative that communicates your findings with precision and professionalism. Your objective is to craft a comprehensive report that not only presents evidence but also demonstrates the rigorous methodology behind your investigative process.
Presenting analysed data requires strategic communication across multiple formats, including expert reports, technical depositions, and potential courtroom testimony. Construct your presentation with clarity, ensuring that technical complexities are articulated in a manner comprehensible to legal professionals, stakeholders, and non technical audiences. Include visual representations like forensic timelines, data flow diagrams, and annotated screenshots to enhance understanding.
Verifying evidence integrity remains paramount throughout the presentation process. Cross reference your findings with original forensic images, validate hash values, and demonstrate that your investigative methodology preserved the original digital evidence without contamination. Pro tip: Prepare a comprehensive chain of custody documentation that tracks every interaction with the evidence, including acquisition, analysis, and storage details.
With your forensic findings professionally presented and evidence integrity rigorously verified, you have completed a comprehensive digital forensic investigation that stands up to the most stringent legal and technical scrutiny.
Elevate Your Digital Forensics Journey with Expert Support
Conducting digital forensics requires meticulous preparation and an unwavering commitment to preserving the integrity of evidence. If you are navigating the challenges of establishing legal authority, securing digital evidence, or analysing complex data sets, you need trusted expertise that understands every step of the investigative process. Our specialised Digital Forensics Examiner services ensure that your evidence is preserved perfectly, analysed thoroughly, and presented with clear, legally defensible documentation.
Do not let critical details slip through the cracks or risk compromising your investigation. Partner with Computer Forensics Lab now to access end-to-end solutions for digital evidence preservation, including advanced techniques and expert witness reporting. Discover how our Digital Evidence Preservation services can bolster your case and maintain chain of custody with absolute confidence. Take the step today to safeguard your digital investigation from start to finish.
Frequently Asked Questions
How do I establish legal authority for a digital forensic investigation?
To establish legal authority, ensure you obtain proper authorisation through warrants, explicit consent, or organisational policies before accessing any digital systems. Work closely with legal counsel to navigate specific consent requirements that apply to your investigations.
What equipment do I need to prepare for conducting digital forensics?
Prepare equipment such as write blockers, forensic workstations, evidence collection drives, and specialised software to prevent data modification. Document each piece of equipment used, including serial numbers and configurations, to maintain a clear chain of custody.
How do I securely identify and preserve digital evidence?
Use a systematic approach to locate and secure potential digital evidence sources, including computers, mobile devices, and cloud storage. Always create forensic images of digital media using write blockers to ensure the original data remains untouched.
What steps should I follow to analyse collected data in digital forensics?
Select comprehensive forensic analysis tools to examine the digital images for hidden patterns and recover deleted information. Document each analysis step and cross-reference findings across different tools to validate your observations.
How can I maintain the chain of custody during a digital forensic investigation?
Maintain the chain of custody by meticulously documenting every action taken, such as timestamps for device acquisition and specific findings. Create detailed custody logs that capture who handled the evidence and under what circumstances to establish integrity and transparency.
What should be included in my final forensic report?
Your forensic report should present a clear narrative of your findings and demonstrate the methodologies behind the investigative process. Include visual aids and comprehensive documentation that tracks every interaction with the evidence, ensuring clarity for both technical and non-technical audiences.