Email investigations are often portrayed as tech-heavy puzzles, where one missed detail can throw off the whole case. Here is the surprise. A successful outcome does not start with clever detective work deep in the inbox but with something far simpler. Everything hinges on setting up the right tools, permissions and protocols before the first email is ever opened. In fact, forensic best practice requires a documented investigation scope and explicit legal permissions before collecting a single message. Most rush past this step, never realising just how much it shapes what you can prove later.
Table of Contents
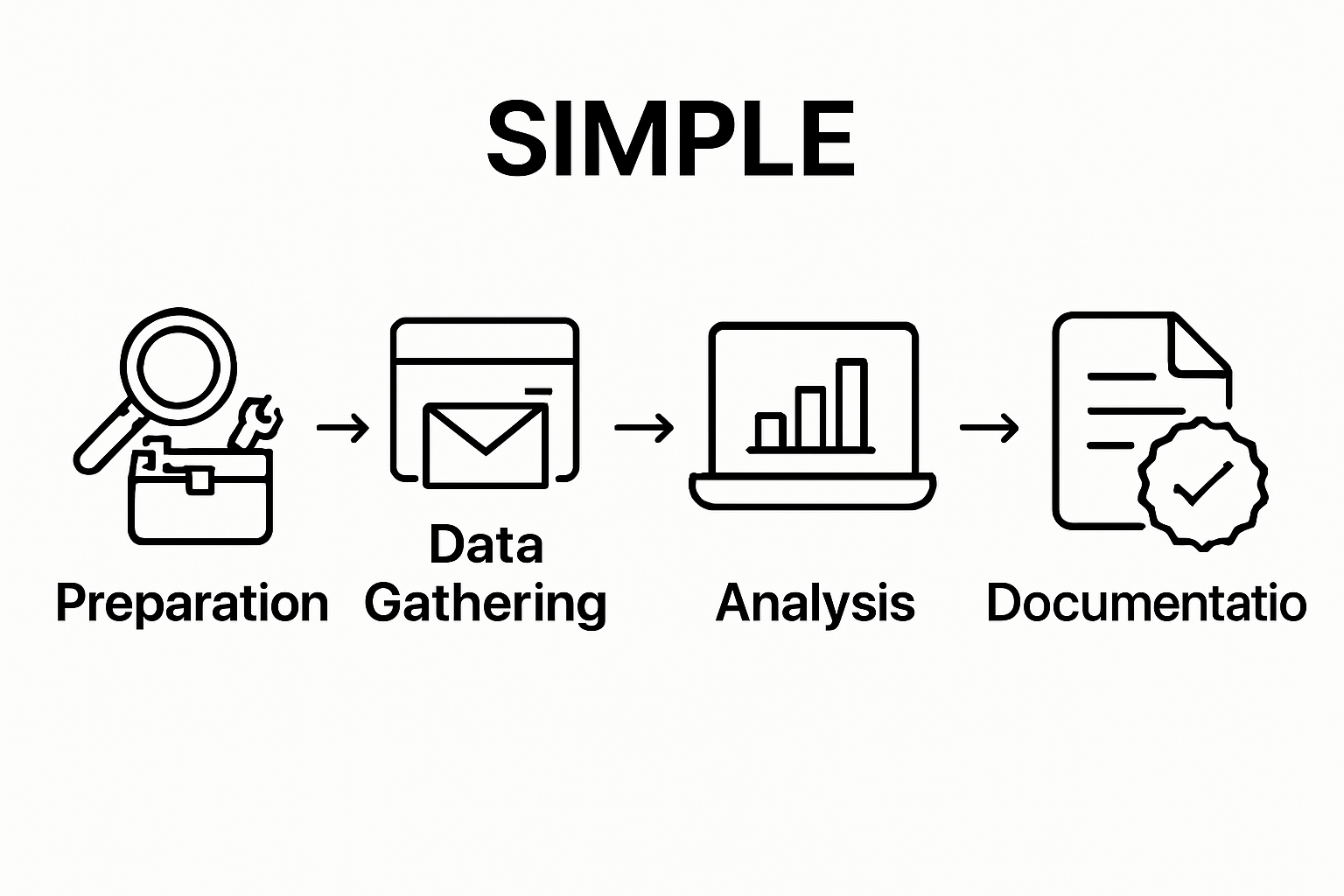
- Step 1: Prepare Your Investigation Tools And Resources
- Step 2: Gather Relevant Email Data And Context
- Step 3: Analyse The Collected Email Information
- Step 4: Document Findings And Create A Report
- Step 5: Verify Accuracy Of Analysis And Conclusions
Quick Summary
| Key Point | Explanation |
|---|---|
| 1. Establish a robust investigation framework | Prepare both technical tools and legal authorisation before starting any investigation to ensure effectiveness and legal compliance. |
| 2. Assemble a comprehensive forensic toolkit | Select specialised hardware and software to preserve evidence integrity and ensure proper documentation throughout the investigation process. |
| 3. Collect detailed email data methodically | Utilize multiple retrieval channels to capture not only message content but also critical metadata essential for effective analysis. |
| 4. Perform in-depth analysis of collected emails | Examine metadata and communication patterns to uncover hidden insights that support the investigative narrative while maintaining objective perspectives. |
| 5. Rigorously verify findings and conclusions | Implement systematic cross-referencing and independent validations to establish the reliability of investigative conclusions and enhance credibility. |
Step 1: Prepare Your Investigation Tools and Resources
Launching a successful email investigation demands meticulous preparation and strategic resource allocation. Investigators must establish a robust technical and legal framework before commencing any digital forensic examination. This critical first step determines the effectiveness and legal admissibility of subsequent investigative actions.
Essential Digital Forensic Toolkit
Building a comprehensive investigation toolkit requires careful selection of hardware and software specifically designed for forensic email analysis. Digital forensics professionals typically rely on specialised software capable of preserving email metadata, extracting communication records, and maintaining strict chain of evidence standards. Key tools often include forensic imaging software, email extraction utilities, and preservation platforms that ensure complete data integrity.
Critical software components for your email investigation workflow should incorporate:
- Forensic email analysis platforms with comprehensive metadata extraction
- Secure evidence preservation and chain of custody tracking systems
- Advanced data recovery and decryption utilities
- Legal compliance monitoring and reporting modules
According to National Institute of Justice research, successful digital investigations hinge on establishing clear procedural protocols before commencing evidence collection. Investigators must verify their technical capabilities align with legal requirements and maintain rigorous documentation throughout the process.
Preparing your investigative environment involves more than technological readiness. Legal authorisation, proper documentation, and understanding potential privacy constraints are equally paramount. Professionals must confirm they possess appropriate permissions for email examination, whether conducting internal corporate investigations or supporting law enforcement objectives.
Before initiating any email investigation, confirm you have comprehensive documentation including precise investigation scope, authorisation credentials, and explicit legal permissions. These foundational elements protect both the investigative process and the potential subsequent legal proceedings. Carefully document every preparatory step, ensuring transparent and defensible investigative methodology.
Successful preparation transforms a potentially complex email investigation into a structured, methodical process. By investing time in comprehensive toolkit assembly and procedural planning, digital forensics professionals set the stage for thorough, legally sound evidence collection and analysis.
Below is an overview table summarising each critical step in the email investigation workflow, including the main action focus and the objective achieved at each stage.
| Step | Main Focus | Key Objective |
|---|---|---|
| 1. Prepare Tools and Resources | Establish toolkit and legal authorisation | Ensure readiness, compliance and defensible investigation |
| 2. Gather Email Data and Context | Capture emails and comprehensive metadata | Collect robust, intact records for analysis |
| 3. Analyse Collected Information | Examine content, metadata, and patterns | Extract meaningful insights and uncover evidence |
| 4. Document Findings and Report | Create structured, clear narrative | Present findings accessibly for legal review |
| 5. Verify Analysis and Conclusions | Independent, systematic validation | Confirm integrity, reliability and defensibility |
Step 2: Gather Relevant Email Data and Context
Email data collection represents a pivotal phase in digital forensic investigations, requiring systematic and precise extraction of communication records. This critical step transforms raw communication data into actionable investigative intelligence, providing comprehensive insights into digital correspondence patterns and potential evidence.
Comprehensive Email Evidence Collection
Investigators must approach email data gathering with methodical precision, understanding that every digital communication fragment could hold crucial investigative significance. Forensic email collection demands capturing multiple layers of information beyond simple message content. This includes intricate metadata such as transmission timestamps, sender and recipient IP addresses, email routing information, and embedded attachment details.
Effective data collection strategies encompass multiple retrieval channels:
- Original email server archives
- Cloud email platform backups
- Local computer email client storage
- Network email transaction logs
- Preserved email account snapshots
According to US Department of Justice forensic guidelines, comprehensive email investigations require meticulous preservation of complete communication context. This means capturing not just individual messages but entire communication threads, associated metadata, and potential contextual attachments that might provide additional investigative insights.
Technical extraction processes must prioritise forensic integrity. Investigators should utilise specialised forensic tools capable of creating exact digital replicas of email repositories without altering original data structures. This approach ensures evidential admissibility and maintains strict chain of custody requirements for potential legal proceedings.
While gathering email data, professionals must remain cognisant of potential privacy regulations and legal constraints. Each data collection action should be explicitly documented, recording precise collection methodologies, timestamps, and authentication processes. Comprehensive documentation protects the investigation’s legal standing and provides transparent evidence of responsible digital forensic practices.
Successful email data gathering transforms scattered digital communications into a coherent investigative narrative. By capturing comprehensive communication records with technical precision and legal conscientiousness, digital forensics professionals build robust foundations for subsequent analytical processes.
The table below outlines typical sources of email evidence used in forensic investigations, along with their respective contents and advantages for investigation.
| Evidence Source | Content Collected | Investigation Value |
|---|---|---|
| Original email server archives | Complete communication threads, metadata | Highest integrity, official records |
| Cloud email platform backups | Email content, attachments, account settings | Redundancy, potential recovery of deleted data |
| Local computer email client storage | Emails, contact lists, cached data | May contain user artefacts, offline evidence |
| Network email transaction logs | Transmission records, routing metadata | Technical validation, trace email flow |
| Preserved email account snapshots | Frozen state of all inbox content | Evidence immutability, aids repeat analysis |
Step 3: Analyse the Collected Email Information
Email information analysis transforms raw digital communication data into meaningful investigative insights. This critical stage involves systematic examination of collected email records, uncovering hidden patterns, potential evidence, and contextual relationships that might reveal crucial investigative information.
Forensic analysis requires a multifaceted approach that goes beyond surface-level message content. Digital investigators must meticulously dissect email metadata, examining transmission routes, communication patterns, embedded technologies, and potential digital fingerprints. Each email represents a complex digital artifact containing layers of potentially significant information.
Key analytical strategies focus on identifying:
- Unusual communication patterns
- Suspicious sender characteristics
- Potential malicious attachments or embedded links
- Hidden metadata inconsistencies
- Network transmission anomalies
According to National Institute of Justice research, effective email analysis requires correlating digital evidence with broader investigative context. Professionals must look beyond individual messages, constructing comprehensive communication narratives that reveal underlying behavioural patterns or potential investigative leads.
Technical examination involves leveraging advanced forensic tools capable of performing deep structural analysis. Sophisticated email forensic platforms can decode complex email headers, trace original transmission routes, and extract granular metadata that might escape casual observation. Investigators should pay special attention to seemingly innocuous details like timestamp discrepancies, routing information, and embedded technological signatures.
The analytical process demands both technical expertise and investigative intuition. Digital forensics professionals must maintain objective analytical perspectives, recognising that email communications represent complex human interactions encoded within digital frameworks. Each analysed email becomes a potential piece of a larger investigative puzzle, requiring careful interpretation and contextual understanding.

Successful email information analysis transforms disconnected digital fragments into coherent investigative narratives. By applying rigorous technical examination and nuanced interpretative skills, digital forensics professionals uncover hidden insights that can substantively advance investigative objectives. The goal transcends mere data collection, focusing instead on extracting meaningful, actionable intelligence from digital communication records.
Step 4: Document Findings and Create a Report
Documenting investigative findings represents the critical final stage of an email investigation, transforming complex digital analysis into a clear, legally defensible narrative. This step bridges technical examination and potential legal or organisational action, requiring precision, clarity, and comprehensive professional communication.
Compiling a forensically sound report demands more than simple data recitation. Digital forensics professionals must construct a narrative that explains technical findings in accessible language, providing context, methodological transparency, and explicit reasoning behind each investigative conclusion. The report serves as an authoritative record that can withstand potential legal scrutiny and professional review.
Critical report components should include:
- Comprehensive investigation methodology
- Detailed chronological evidence timeline
- Technical tools and processes employed
- Specific findings and their investigative significance
- Potential recommendations or implications
According to National Institute of Standards and Technology guidelines, effective documentation requires meticulous attention to procedural transparency. Each investigative action must be explicitly recorded, demonstrating a clear, reproducible process that validates the investigation’s technical and legal integrity.
Reporting goes beyond merely listing discovered information. Skilled investigators craft a narrative that contextualises digital evidence, explaining not just what was found, but how and why specific conclusions were reached. This approach transforms raw data into meaningful insights that can support legal proceedings, internal investigations, or organisational decision making.
Technical language must be balanced with clarity, ensuring that non-technical stakeholders can comprehend the report’s significance. Investigators should anticipate potential questions, providing preemptive explanations of complex technical processes and their relevance to the broader investigative context. Visual elements like diagrams, communication flow charts, and structured timelines can enhance report comprehension.
Ultimate report success is measured by its ability to communicate complex digital forensic findings with precision and professionalism. A well-constructed report not only documents investigative discoveries but also establishes the credibility of the digital forensics process, serving as a critical bridge between technical investigation and potential legal or organisational action.
Step 5: Verify Accuracy of Analysis and Conclusions
Verification represents the ultimate quality control mechanism in digital forensic email investigations, ensuring the reliability and integrity of investigative findings. This crucial step transforms preliminary conclusions into legally defensible and scientifically robust evidence by subjecting the entire investigative process to rigorous independent scrutiny.
Comprehensive verification demands a systematic approach that goes beyond simple data rechecking. Digital forensics professionals must critically examine their methodological choices, analytical processes, and ultimate conclusions with objective, dispassionate precision. This involves creating multiple independent validation pathways that challenge and confirm initial investigative insights.
Key verification strategies include:
- Cross-referencing findings with alternative forensic tools
- Conducting independent duplicate analysis
- Reviewing evidence chain of custody documentation
- Testing initial hypotheses against contradictory evidence scenarios
- Soliciting peer review from external forensic experts
According to US Department of Justice forensic guidelines, effective verification requires a structured approach that systematically challenges investigative assumptions. Professionals must demonstrate not just what was discovered, but why and how those conclusions were reached, ensuring transparency and scientific reproducibility.
Technical verification involves employing multiple forensic platforms and analytical techniques to corroborate initial findings. Investigators should deliberately use different software tools and methodological approaches, seeking consistent results that eliminate potential technological biases. This multi-vector validation significantly enhances the credibility of digital forensic investigations.
The following checklist table breaks down the crucial verification actions required to ensure the accuracy and reliability of email forensic investigation findings.
| Verification Action | Purpose | Result |
|---|---|---|
| Cross-reference findings | Validate results using alternative tools | Confirms consistent conclusions |
| Independent duplicate analysis | Replicate processes independently | Eliminates procedural error |
| Review chain of custody records | Confirm evidence handling integrity | Ensures admissibility and audit trail |
| Test against contradictory scenarios | Challenge existing hypotheses | Strengthens objectivity and defensibility |
| External peer review | Gain third-party evaluation | Reduces bias, ensures scientific rigour |
Psychological awareness plays a critical role in verification. Cognitive bias can unconsciously influence investigative conclusions, making independent review essential. Experienced digital forensics professionals cultivate a mindset of constructive skepticism, actively seeking perspectives that might challenge their initial interpretations.
Successful verification transforms preliminary investigative findings into reliable, defensible digital evidence. By subjecting email investigation conclusions to systematic, multi-layered validation, digital forensics professionals ensure the highest standards of technical and legal integrity. The verification process is not about proving oneself correct, but about rigorously establishing the objective truth embedded within complex digital communication records.
Elevate Your Email Investigations With Professional Digital Forensic Support
Struggling to keep your email evidence reliable and legally admissible? As detailed in this guide, mastering the step-by-step workflow of email investigation—from securing forensic tools and preserving chain of custody to analysing metadata and reporting—is complex and filled with risk. Many investigators and organisations worry about missing hidden data, breaching privacy rules, or failing to create a defensible case. If you are aiming for robust results and peace of mind, expert help is essential. Discover how the Digital Forensic Investigation specialists at Computer Forensics Lab can bridge the gap between technical detail and legal certainty.
Do not leave your investigation open to error. Whether you face digital fraud, internal employee misconduct, IP theft, or litigation, rely on the trusted specialists at Computer Forensics Lab in London. Accelerate your case with advanced forensic tools, precise evidence documentation, and comprehensive report writing. Ready to secure your findings and defend your conclusions? Visit our Digital Forensic Investigation page or get expert advice from Computer Forensics Lab now for immediate, confidential assistance.
Frequently Asked Questions
What tools are essential for conducting an email investigation?
A comprehensive email investigation toolkit should include forensic email analysis platforms, secure evidence preservation systems, advanced data recovery utilities, and legal compliance monitoring tools to ensure data integrity and chain of custody.
How can I ensure the legal admissibility of my email investigation findings?
To ensure legal admissibility, document every step of the investigation, maintain chain of custody, and obtain necessary legal permissions and authorisations before collecting email data.
What should I focus on during the analysis of collected email information?
During analysis, focus on identifying unusual communication patterns, examining email metadata, recognising suspicious senders, and detecting hidden inconsistencies to uncover significant investigative insights.
Why is verification important in an email investigation?
Verification is crucial as it serves as a quality control measure, ensuring the reliability and integrity of findings. It involves independent scrutiny of methods and conclusions to confirm accuracy and establish defensibility in potential legal proceedings.
Recommended
- Cloud Forensics Step by Step: Mastering Digital Investigations
- Definitive Guide To Social Media Forensics
- Inside the World of a Hacking Forensic Investigator -Computer Hacking
- Mobile Phone Hacking Investigation for Private and Business Clients | Computer Forensics Lab | Digital Forensics Services | Digital Detectives
- Email Campaigns and SEO: Winning Strategies for 2025
- Understanding Email Marketing Strategies for Businesses | Marketing Car Blog
