Most UK corporations now face escalating risks from digital threats, with more than two thirds reporting a surge in internal cyber investigations over the past year. Keeping sensitive business data secure is no longer just a technical issue, it is a serious operational and legal priority for every organisation. This guide demystifies digital forensics for british companies, revealing how expert analysis and evidence handling unlock answers to complex workplace incidents and cybersecurity disputes.
Table of Contents
- Digital Forensics Explained For Corporates
- Types Of Digital Evidence In Investigations
- Typical Processes And Forensic Methodologies
- Legal Obligations And Evidentiary Standards
- Risks, Pitfalls, And Preserving Integrity
Key Takeaways
| Point | Details |
|---|---|
| Digital Forensics Importance | Digital forensics is essential for corporations to uncover evidence during investigations, addressing misconduct and compliance issues. |
| Types of Digital Evidence | Key categories include device artefacts, network communications, metadata, and cloud storage data, each requiring rigorous handling to ensure legal admissibility. |
| Methodological Rigor | Investigations follow a systematic process, including evidence identification, preservation, extraction, analysis, and documentation to maintain integrity. |
| Legal Compliance | Forensic experts must adhere to strict legal obligations, including maintaining chain of custody and ensuring data protection, to ensure evidence is admissible in court. |
Digital forensics explained for corporates
Digital forensics represents a sophisticated investigative approach that enables corporations to uncover critical electronic evidence during internal and legal investigations. By systematically collecting, preserving, and analysing digital data from multiple sources, organisations can effectively investigate potential misconduct, intellectual property theft, and compliance breaches.
At its core, digital forensics involves detailed examination of computer systems, networks, mobile devices, and digital storage media to extract forensically sound evidence. Corporate investigations leverage sophisticated digital forensics techniques that include comprehensive system audits, email communication analysis, network traffic monitoring, and advanced data recovery processes. These methodologies help businesses understand the precise sequence of digital interactions, identify potential security vulnerabilities, and reconstruct digital events with remarkable precision.
The primary objectives of digital forensics in corporate settings encompass several critical domains:
- Evidence Collection: Retrieving digital records while maintaining strict chain of custody protocols
- Data Preservation: Ensuring original digital artifacts remain unaltered during investigation
- Forensic Analysis: Examining digital traces to understand user actions and system interactions
- Compliance Documentation: Creating detailed forensic reports admissible in legal proceedings
Corporate legal teams and investigators increasingly rely on these forensic techniques to address complex challenges such as employee misconduct, cybersecurity incidents, intellectual property disputes, and regulatory compliance investigations. By employing rigorous scientific methodologies, digital forensics transforms raw electronic data into actionable intelligence that can protect an organisation’s interests and support strategic decision-making.
Types of digital evidence in investigations
Digital evidence represents the foundational backbone of modern investigative processes, encompassing a wide range of electronic information that can be critical in legal and corporate contexts. Digital forensic experts meticulously collect and analyse various types of electronic data that can uncover crucial insights during investigations.
The primary categories of digital evidence include:
- Device Artefacts: Data from computers, smartphones, tablets, and external storage devices
- Network Communications: Email records, instant messaging logs, network traffic logs
- Metadata: Hidden information embedded within digital files revealing creation, modification, and access details
- System Logs: Records of user activities, system events, and login attempts
- Cloud Storage Data: Information stored in online platforms and cloud services
Each digital evidence type requires sophisticated forensic techniques to extract, preserve, and analyse without compromising its legal admissibility. Forensic professionals must follow strict protocols to maintain the integrity of electronic data, ensuring that the evidence can withstand rigorous legal scrutiny.
The complexity of digital evidence collection demands advanced technological capabilities and deep understanding of digital systems. Investigators must navigate intricate technical landscapes, decrypting complex data structures, recovering deleted files, and reconstructing digital timelines that can reveal critical information about potential corporate misconduct, cybersecurity breaches, or legal disputes.
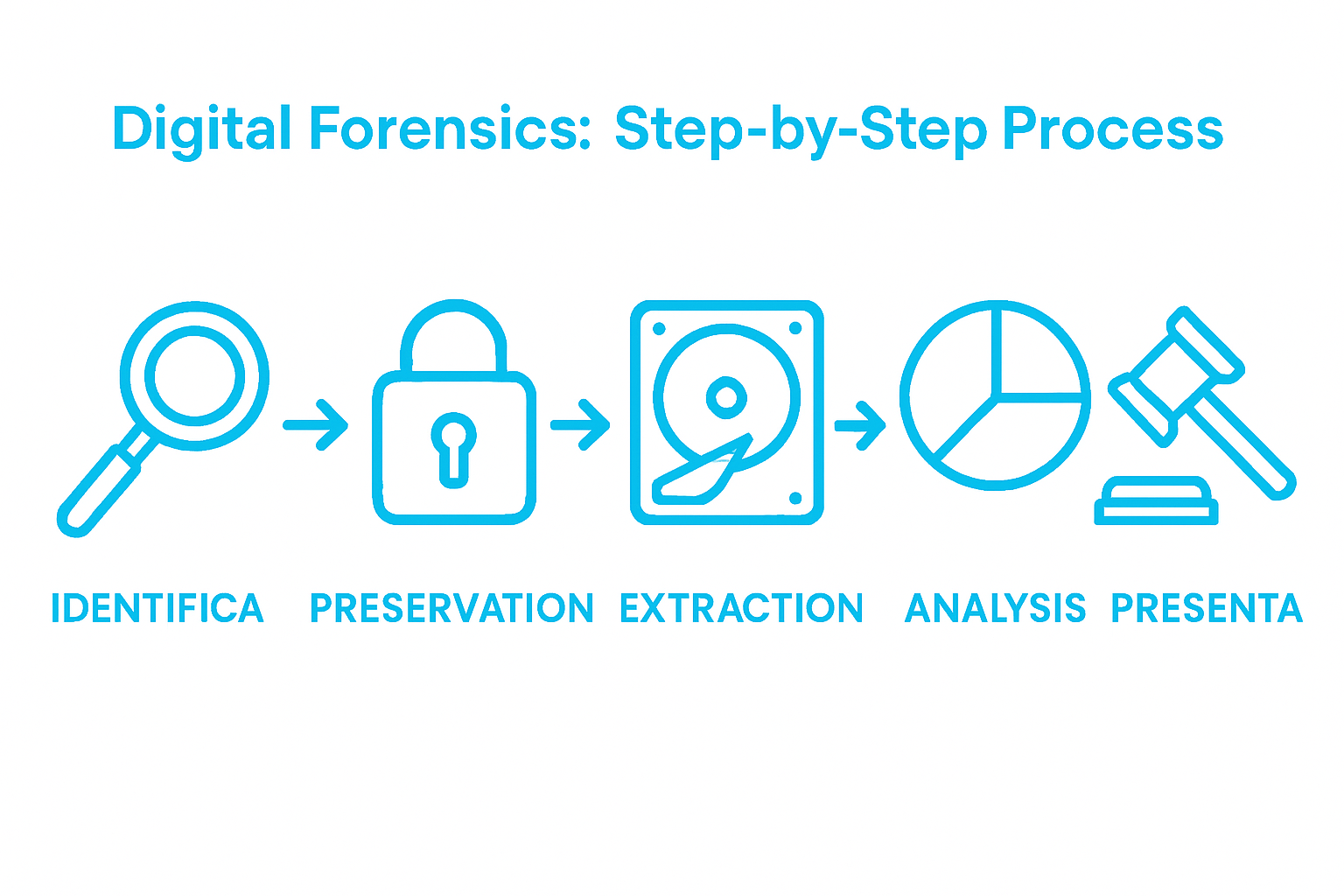
Typical processes and forensic methodologies
Digital forensic investigations follow a systematic and rigorous methodology designed to ensure the integrity and admissibility of electronic evidence. Forensic professionals employ sophisticated techniques for decrypting, recovering, and analysing digital artefacts across multiple technological platforms.
The standard digital forensic process typically encompasses several critical stages:
- Evidence Identification: Locating and securing potential digital sources
- Evidence Preservation: Creating forensically sound bit-by-bit copies of original data
- Evidence Extraction: Recovering deleted, hidden, or encrypted information
- Evidence Analysis: Systematically examining digital traces and reconstructing events
- Evidence Documentation: Generating comprehensive forensic reports with detailed findings
Forensic methodologies require extraordinary technical precision, combining advanced technological skills with meticulous investigative techniques. Investigators must maintain strict chain of custody protocols, ensuring that digital evidence remains uncontaminated and legally admissible throughout the investigative process.
The complexity of modern digital environments demands continuous adaptation of forensic techniques. Professionals must navigate intricate technological landscapes, addressing challenges presented by cloud computing, encrypted communications, and increasingly sophisticated cybersecurity mechanisms. Their work bridges technological expertise with legal requirements, transforming raw digital data into coherent, legally defensible narratives that can withstand intense judicial scrutiny.
Legal obligations and evidentiary standards
Digital forensic investigations operate within a complex legal framework that demands absolute precision and adherence to stringent evidentiary standards. Privacy-oriented threat modeling has become increasingly crucial in ensuring the legal integrity of digital evidence collection processes, requiring forensic professionals to navigate intricate legal and ethical challenges.
Key legal obligations for digital forensic experts encompass several critical domains:
- Chain of Custody: Maintaining unbroken documentation of evidence handling
- Evidence Integrity: Ensuring digital artefacts remain unaltered and forensically sound
- Data Protection: Respecting individual privacy rights during investigations
- Procedural Compliance: Following legally approved forensic methodologies
- Admissibility Standards: Preparing evidence that meets judicial scrutiny
Forensic professionals must demonstrate meticulous documentation of every investigative step, creating comprehensive audit trails that can withstand intense legal examination. This requires not only technical expertise but also a profound understanding of legal frameworks governing digital evidence, including data protection regulations, human rights considerations, and specific rules of evidence applicable in different jurisdictions.
The evolving digital landscape continually challenges existing legal standards, demanding that forensic experts remain adaptable and proactive. They must balance technological capabilities with legal constraints, ensuring that sophisticated investigative techniques do not compromise individual privacy rights or legal procedural requirements. This delicate balance requires ongoing training, deep ethical commitment, and a nuanced understanding of both technological and legal domains.
Risks, pitfalls, and preserving integrity
Digital forensic investigations are fraught with complex technical and procedural challenges that can potentially compromise evidence integrity. Cloud computing environments have fundamentally transformed digital forensic methodologies, introducing unprecedented research challenges that demand continuous adaptation and sophisticated investigative strategies.
The primary risks and potential pitfalls in digital forensic investigations include:
- Data Contamination: Accidental modification of original digital evidence
- Technical Limitations: Inability to access encrypted or complex storage systems
- Rapid Technology Changes: Obsolescence of forensic tools and techniques
- Cross-Platform Complexity: Investigating evidence across multiple technological ecosystems
- Jurisdictional Constraints: Legal restrictions on digital evidence collection
Forensic professionals must implement robust preservation protocols that safeguard digital evidence from potential corruption. This requires advanced technical skills, meticulous documentation, and an unwavering commitment to maintaining the original state of digital artefacts throughout the investigative process.
The dynamic nature of digital technologies necessitates continuous learning and adaptation. Investigators must remain vigilant, anticipating potential technological challenges and developing innovative strategies to overcome emerging obstacles. Their work demands not just technical expertise, but also a profound understanding of the intricate relationships between technological capabilities, legal frameworks, and ethical considerations.
Strengthen Your Corporate Investigations with Expert Digital Forensics Support
When dealing with complex corporate challenges such as employee misconduct, intellectual property theft, or cybersecurity breaches, it is crucial to have precise and legally sound digital evidence. The article highlights key concerns around evidence preservation, chain of custody, and the need for expert forensic analysis to uncover hidden digital truths. Without the right expertise, vital data can be compromised or overlooked, putting your organisation at risk both legally and reputationally.
At Computer Forensics Lab, we specialise in Corporate Forensic Investigations that address these exact challenges. Our expert team utilises advanced techniques to recover and analyse digital data from computers, mobile devices, cloud services, and networks. We ensure all evidence is collected with forensic integrity and comprehensive documentation to support your legal needs. Explore how our Corporate Forensic Investigations service can safeguard your organisation through meticulous digital forensic processes.
Do not leave critical corporate investigations to chance. Visit Computer Forensics Lab today to discover how our reliable forensic solutions and clear expert witness reports can empower your legal and compliance teams. Take the next step to protect your business interests and maintain regulatory compliance now.
Frequently Asked Questions
What is digital forensics in corporate investigations?
Digital forensics in corporate investigations involves systematically collecting, preserving, and analysing digital data to uncover electronic evidence related to misconduct, security breaches, or compliance violations within an organisation.
What types of digital evidence are typically collected during investigations?
Digital evidence can include device artefacts such as data from computers and smartphones, network communications like email logs, metadata, system logs, and data stored in cloud services, all of which are critical for legal and corporate investigations.
What are the primary stages in a digital forensic investigation?
The standard stages of a digital forensic investigation include evidence identification, preservation, extraction, analysis, and documentation, all of which ensure that digital evidence is handled properly and remains legally admissible.
What legal obligations must digital forensic investigators adhere to?
Digital forensic investigators must maintain a strict chain of custody for evidence, ensure the integrity of digital artefacts, respect data protection regulations, and follow legally approved methodologies to prepare evidence that can withstand judicial scrutiny.
Recommended
- Corporate Forensics Investigations For UK Companies | Computer Forensics Lab | Digital Forensics Services
- 7 Top Digital Forensics Techniques Every Legal Team Must Know
- UK Digital Forensic Investigations Guide
- 7 Essential Digital Forensic Techniques for Success
- Complete Guide to the Role of Forensic Engineering – FloridaLicensedEngineers.com